Fortinet FCP_FGT_AD-7.4 Übungsprüfungen
Zuletzt aktualisiert am 26.04.2025- Prüfungscode: FCP_FGT_AD-7.4
- Prüfungsname: FCP - FortiGate 7.4 Administrator
- Zertifizierungsanbieter: Fortinet
- Zuletzt aktualisiert am: 26.04.2025
Refer to exhibit.
An administrator configured the web filtering profile shown in the exhibit to block access to all social networking sites except Twitter. However, when users try to access twitter.com, they are redirected to a FortiGuard web filtering block page.
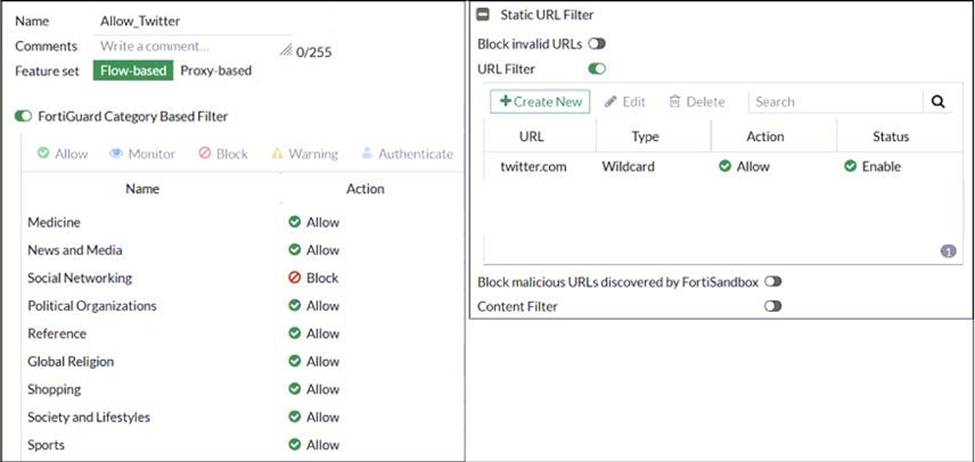
Based on the exhibit, which configuration change can the administrator make to allow Twitter while blocking all other social networking sites?
- A . On the FortiGuard Category Based Filter configuration, set Action to Warning for Social Networking.
- B . On the Static URL Filter configuration, set Type to Simple.
- C . On the Static URL Filter configuration, set Action to Exempt.
- D . On the Static URL Filter configuration, set Action to Monitor.
Which two settings are required for SSL VPN to function between two FortiGate devices? (Choose two.)
- A . The client FortiGate requires a manually added route to remote subnets.
- B . The client FortiGate requires a client certificate signed by the CA on the server FortiGate.
- C . The server FortiGate requires a CA certificate to verify the client FortiGate certificate.
- D . The client FortiGate requires the SSL VPN tunnel interface type to connect SSL VPN.
Which two statements are true about the FGCP protocol? (Choose two.)
- A . FGCP elects the primary FortiGate device.
- B . FGCP is not used when FortiGate is in transparent mode.
- C . FGCP runs only over the heartbeat links.
- D . FGCP is used to discover FortiGate devices in different HA groups.
Which downstream FortiGate VDOM is used to join the Security Fabric when split-task VDOM is enabled on all FortiGate devices?
- A . FG-traffic VDOM
- B . Root VDOM
- C . Customer VDOM
- D . Global VDOM
Which three criteria can FortiGate use to look for a matching firewall policy to process traffic? (Choose three.)
- A . Services defined in the firewall policy
- B . Highest to lowest priority defined in the firewall policy
- C . Destination defined as Internet Services in the firewall policy
- D . Lowest to highest policy ID number
- E . Source defined as Internet Services in the firewall policy
Which two attributes are required on a certificate so it can be used as a CA certificate on SSL inspection? (Choose two.)
- A . The keyUsage extension must be set to keyCertSign.
- B . The CA extension must be set to TRUE.
- C . The issuer must be a public CA.
- D . The common name on the subject field must use a wildcard name.
An administrator has configured central DNAT and virtual IPs.
Which item can be selected in the firewall policy Destination field?
- A . An IP pool
- B . A VIP object
- C . A VIP group
- D . The mapped IP address object of the VIP object
Which three statements explain a flow-based antivirus profile? (Choose three.)
- A . Flow-based inspection uses a hybrid of the scanning modes available in proxy-based inspection.
- B . If a virus is detected, the last packet is delivered to the client.
- C . The IPS engine handles the process as a standalone.
- D . FortiGate buffers the whole file but transmits to the client at the same time.
- E . Flow-based inspection optimizes performance compared to proxy-based inspection.
Refer to the exhibit.
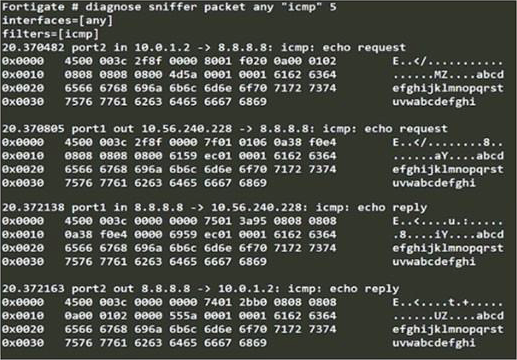
An administrator is running a sniffer command as shown in the exhibit.
Which three pieces of information are included in the sniffer output? (Choose three.)
- A . Interface name
- B . Ethernet header
- C . IP header
- D . Application header
- E . Packet payload
Which two inspection modes can you use to configure a firewall policy on a profile-based next-generation firewall (NGFW)? (Choose two.)
- A . Proxy-based inspection
- B . Certificate inspection
- C . Flow-based inspection
- D . Full Content inspection
