CompTIA CAS-005 Übungsprüfungen
Zuletzt aktualisiert am 24.04.2025- Prüfungscode: CAS-005
- Prüfungsname: CompTIA SecurityX Certification Exam
- Zertifizierungsanbieter: CompTIA
- Zuletzt aktualisiert am: 24.04.2025
Within a SCADA a business needs access to the historian server in order together metric about the functionality of the environment.
Which of the following actions should be taken to address this requirement?
- A . Isolating the historian server for connections only from The SCADA environment
- B . Publishing the C$ share from SCADA to the enterprise
- C . Deploying a screened subnet between 11 and SCADA
- D . Adding the business workstations to the SCADA domain
A financial technology firm works collaboratively with business partners in the industry to share threat intelligence within a central platform This collaboration gives partner organizations the ability to obtain and share data associated with emerging threats from a variety of adversaries.
Which of the following should the organization most likely leverage to facilitate this activity? (Select two).
- A . CWPP
- B . YAKA
- C . ATTACK
- D . STIX
- E . TAXII
- F . JTAG
The material finding from a recent compliance audit indicate a company has an issue with excessive permissions. The findings show that employees changing roles or departments results in privilege creep.
Which of the following solutions are the best ways to mitigate this issue? (Select two). Setting different access controls defined by business area
- A . Implementing a role-based access policy
- B . Designing a least-needed privilege policy
- C . Establishing a mandatory vacation policy
- D . Performing periodic access reviews
- E . Requiring periodic job rotation
All organization is concerned about insider threats from employees who have individual access to encrypted material.
Which of the following techniques best addresses this issue?
- A . SSO with MFA
- B . Sating and hashing
- C . Account federation with hardware tokens
- D . SAE
- E . Key splitting
Users must accept the terms presented in a captive petal when connecting to a guest network. Recently, users have reported that they are unable to access the Internet after joining the network
A network engineer observes the following:
• Users should be redirected to the captive portal.
• The Motive portal runs Tl. S 1 2
• Newer browser versions encounter security errors that cannot be bypassed
• Certain websites cause unexpected re directs
Which of the following mow likely explains this behavior?
- A . The TLS ciphers supported by the captive portal ate deprecated
- B . Employment of the HSTS setting is proliferating rapidly.
- C . Allowed traffic rules are causing the NIPS to drop legitimate traffic
- D . An attacker is redirecting supplicants to an evil twin WLAN.
Recent repents indicate that a software tool is being exploited Attackers were able to bypass user access controls and load a database. A security analyst needs to find the vulnerability and recommend a mitigation.
The analyst generates the following output:

Which of the following would the analyst most likely recommend?
- A . Installing appropriate EDR tools to block pass-the-hash attempts
- B . Adding additional time to software development to perform fuzz testing
- C . Removing hard coded credentials from the source code
- D . Not allowing users to change their local passwords
A security architect for a global organization with a distributed workforce recently received funding lo deploy a CASB solution.
Which of the following most likely explains the choice to use a proxy-based CASB?
- A . The capability to block unapproved applications and services is possible
- B . Privacy compliance obligations are bypassed when using a user-based deployment.
- C . Protecting and regularly rotating API secret keys requires a significant time commitment
- D . Corporate devices cannot receive certificates when not connected to on-premises devices
A company hosts a platform-as-a-service solution with a web-based front end, through which customer interact with data sets. A security administrator needs to deploy controls to prevent application-focused attacks.
Which of the following most directly supports the administrator’s objective‘
- A . improving security dashboard visualization on SIEM
- B . Rotating API access and authorization keys every two months
- C . Implementing application toad balancing and cross-region availability
- D . Creating WAF policies for relevant programming languages
A security analyst is reviewing the following log:
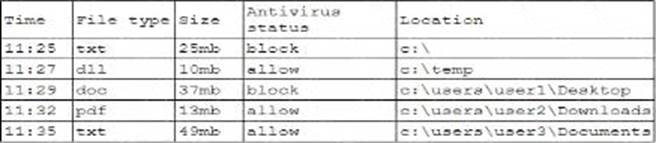
Which of the following possible events should the security analyst investigate further?
- A . A macro that was prevented from running
- B . A text file containing passwords that were leaked
- C . A malicious file that was run in this environment
- D . A PDF that exposed sensitive information improperly
After remote desktop capabilities were deployed in the environment, various vulnerabilities were noticed.
• Exfiltration of intellectual property
• Unencrypted files
• Weak user passwords
Which of the following is the best way to mitigate these vulnerabilities? (Select two).
- A . Implementing data loss prevention
- B . Deploying file integrity monitoring
- C . Restricting access to critical file services only
- D . Deploying directory-based group policies
- E . Enabling modem authentication that supports MFA
- F . Implementing a version control system
- G . Implementing a CMDB platform
