CompTIA CS0-003 Übungsprüfungen
Zuletzt aktualisiert am 26.04.2025- Prüfungscode: CS0-003
- Prüfungsname: CompTIA Cybersecurity Analyst (CySA+) Exam
- Zertifizierungsanbieter: CompTIA
- Zuletzt aktualisiert am: 26.04.2025
The analyst reviews the following endpoint log entry:

Which of the following has occurred?
- A . Registry change
- B . Rename computer
- C . New account introduced
- D . Privilege escalation
A virtual web server in a server pool was infected with malware after an analyst used the internet to research a system issue. After the server was rebuilt and added back into the server pool, users reported issues with the website, indicating the site could not be trusted.
Which of the following is the most likely cause of the server issue?
- A . The server was configured to use SSI- to securely transmit data
- B . The server was supporting weak TLS protocols for client connections.
- C . The malware infected all the web servers in the pool.
- D . The digital certificate on the web server was self-signed
A virtual web server in a server pool was infected with malware after an analyst used the internet to research a system issue. After the server was rebuilt and added back into the server pool, users reported issues with the website, indicating the site could not be trusted.
Which of the following is the most likely cause of the server issue?
- A . The server was configured to use SSI- to securely transmit data
- B . The server was supporting weak TLS protocols for client connections.
- C . The malware infected all the web servers in the pool.
- D . The digital certificate on the web server was self-signed
A development team recently released a new version of a public-facing website for testing prior to
production. The development team is soliciting the help of various teams to validate the functionality of the website due to its high visibility.
Which of the following activities best describes the process the development team is initiating?
- A . Static analysis
- B . Stress testing
- C . Code review
- D . User acceptance testing
A recent vulnerability scan resulted in an abnormally large number of critical and high findings that require patching. The SLA requires that the findings be remediated within a specific amount of time.
Which of the following is the best approach to ensure all vulnerabilities are patched in accordance with the SLA?
- A . Integrate an IT service delivery ticketing system to track remediation and closure.
- B . Create a compensating control item until the system can be fully patched.
- C . Accept the risk and decommission current assets as end of life.
- D . Request an exception and manually patch each system.
A new SOC manager reviewed findings regarding the strengths and weaknesses of the last tabletop exercise in order to make improvements.
Which of the following should the SOC manager utilize to improve the process?
- A . The most recent audit report
- B . The incident response playbook
- C . The incident response plan
- D . The lessons-learned register
Following a recent security incident, the Chief Information Security Officer is concerned with improving visibility and reporting of malicious actors in the environment. The goal is to reduce the time to prevent lateral movement and potential data exfiltration.
Which of the following techniques will best achieve the improvement?
- A . Mean time to detect
- B . Mean time to respond
- C . Mean time to remediate
- D . Service-level agreement uptime
The Chief Information Security Officer for an organization recently received approval to install a new EDR solution. Following the installation, the number of alerts that require remediation by an analyst has tripled.
Which of the following should the organization utilize to best centralize the workload for the internal security team? (Select two).
- A . SOAR
- B . SIEM
- C . MSP
- D . NGFW
- E . XDR
- F . DLP
Which of the following should be updated after a lessons-learned review?
- A . Disaster recovery plan
- B . Business continuity plan
- C . Tabletop exercise
- D . Incident response plan
An analyst needs to provide recommendations based on a recent vulnerability scan:
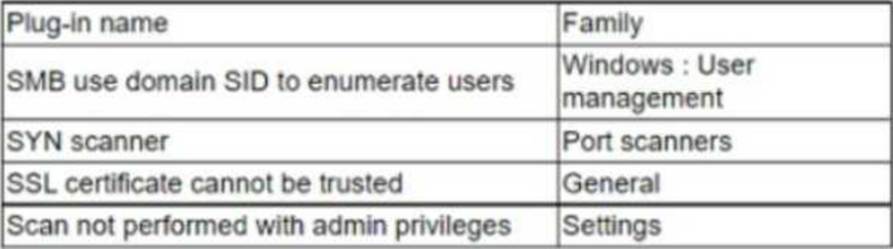
Which of the following should the analyst recommend addressing to ensure potential vulnerabilities are identified?
- A . SMB use domain SID to enumerate users
- B . SYN scanner
- C . SSL certificate cannot be trusted
- D . Scan not performed with admin privileges
