CompTIA CS0-003 Übungsprüfungen
Zuletzt aktualisiert am 27.04.2025- Prüfungscode: CS0-003
- Prüfungsname: CompTIA Cybersecurity Analyst (CySA+) Exam
- Zertifizierungsanbieter: CompTIA
- Zuletzt aktualisiert am: 27.04.2025
A cybersecurity team lead is developing metrics to present in the weekly executive briefs. Executives are interested in knowing how long it takes to stop the spread of malware that enters the network.
Which of the following metrics should the team lead include in the briefs?
- A . Mean time between failures
- B . Mean time to detect
- C . Mean time to remediate
- D . Mean time to contain
An analyst received an alert regarding an application spawning a suspicious command shell process Upon further investigation, the analyst observes the following registry change occurring immediately after the suspicious event:
![]()
Which of the following was the suspicious event able to accomplish?
- A . Impair defenses.
- B . Establish persistence.
- C . Bypass file access controls.
- D . Implement beaconing.
The management team has asked a senior security engineer to explore DLP security solutions for the company’s growing use of cloud-based storage.
Which of the following is an appropriate solution to control the sensitive data that is being stored in the cloud?
- A . NAC
- B . IPS
- C . CASB
- D . WAF
A zero-day command injection vulnerability was published.
A security administrator is analyzing the following logs for evidence of adversaries attempting to exploit the vulnerability:
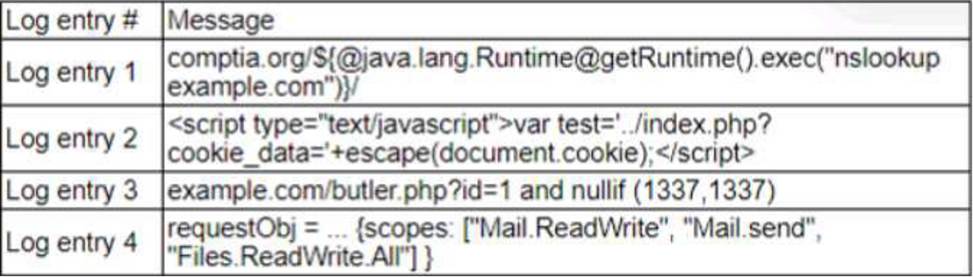
Which of the following log entries provides evidence of the attempted exploit?
- A . Log entry 1
- B . Log entry 2
- C . Log entry 3
- D . Log entry 4
A company has decided to expose several systems to the internet, The systems are currently available internally only. A security analyst is using a subset of CVSS3.1 exploitability metrics to prioritize the vulnerabilities that would be the most exploitable when the systems are exposed to the internet.
The systems and the vulnerabilities are shown below:
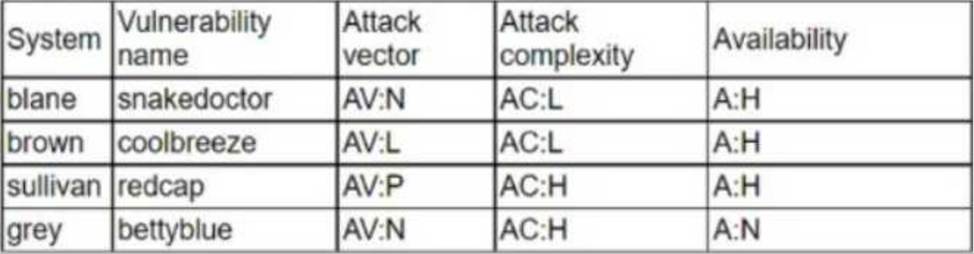
Which of the following systems should be prioritized for patching?
- A . brown
- B . grey
- C . blane
- D . sullivan
A security analyst has found a moderate-risk item in an organization’s point-of-sale application. The organization is currently in a change freeze window and has decided that the risk is not high enough to correct at this time.
Which of the following inhibitors to remediation does this scenario illustrate?
- A . Service-level agreement
- B . Business process interruption
- C . Degrading functionality
- D . Proprietary system
Which of the following threat actors is most likely to target a company due to its questionable environmental policies?
- A . Hacktivist
- B . Organized crime
- C . Nation-state
- D . Lone wolf
During an investigation, an analyst discovers the following rule in an executive’s email client:
![]()
The executive is not aware of this rule.
Which of the following should the analyst do first to evaluate the potential impact of this security incident?
- A . Check the server logs to evaluate which emails were sent to <someaddress@domain,com>.
- B . Use the SIEM to correlate logging events from the email server and the domain server.
- C . Remove the rule from the email client and change the password.
- D . Recommend that the management team implement SPF and DKIM.
A cybersecurity analyst is recording the following details
* ID
* Name
* Description
* Classification of information
* Responsible party
In which of the following documents is the analyst recording this information?
- A . Risk register
- B . Change control documentation
- C . Incident response playbook
- D . Incident response plan
An analyst is reviewing a vulnerability report and must make recommendations to the executive team. The analyst finds that most systems can be upgraded with a reboot resulting in a single downtime window. However, two of the critical systems cannot be upgraded due to a vendor appliance that the company does not have access to.
Which of the following inhibitors to remediation do these systems and associated vulnerabilities best represent?
- A . Proprietary systems
- B . Legacy systems
- C . Unsupported operating systems
- D . Lack of maintenance windows
