CompTIA CS0-003 Übungsprüfungen
Zuletzt aktualisiert am 27.04.2025- Prüfungscode: CS0-003
- Prüfungsname: CompTIA Cybersecurity Analyst (CySA+) Exam
- Zertifizierungsanbieter: CompTIA
- Zuletzt aktualisiert am: 27.04.2025
A security analyst scans a host and generates the following output:
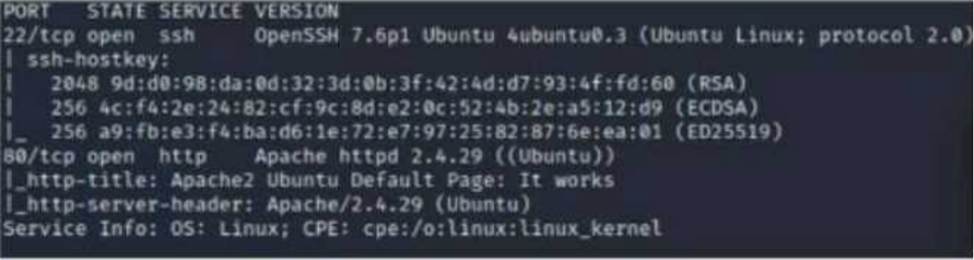
Which of the following best describes the output?
- A . The host is unresponsive to the ICMP request.
- B . The host Is running a vulnerable mall server.
- C . The host Is allowing unsecured FTP connectlons.
- D . The host is vulnerable to web-based exploits.
A security analyst scans a host and generates the following output:

Which of the following best describes the output?
- A . The host is unresponsive to the ICMP request.
- B . The host Is running a vulnerable mall server.
- C . The host Is allowing unsecured FTP connectlons.
- D . The host is vulnerable to web-based exploits.
An analyst is examining events in multiple systems but is having difficulty correlating data points.
Which of the following is most likely the issue with the system?
- A . Access rights
- B . Network segmentation
- C . Time synchronization
- D . Invalid playbook
A network security analyst for a large company noticed unusual network activity on a critical system.
Which of the following tools should the analyst use to analyze network traffic to search for malicious activity?
- A . WAF
- B . Wireshark
- C . EDR
- D . Nmap
A cybersecurity team has witnessed numerous vulnerability events recently that have affected operating systems. The team decides to implement host-based IPS, firewalls, and two-factor authentication.
Which of the following does this most likely describe?
- A . System hardening
- B . Hybrid network architecture
- C . Continuous authorization
- D . Secure access service edge
While a security analyst for an organization was reviewing logs from web servers. the analyst found several successful attempts to downgrade HTTPS sessions to use cipher modes of operation susceptible to padding oracle attacks.
Which of the following combinations of configuration changes should the organization make to remediate this issue? (Select two).
- A . Configure the server to prefer TLS 1.3.
- B . Remove cipher suites that use CBC.
- C . Configure the server to prefer ephemeral modes for key exchange.
- D . Require client browsers to present a user certificate for mutual authentication.
- E . Configure the server to require HSTS.
- F . Remove cipher suites that use GCM.
A security analyst received an alert regarding multiple successful MFA log-ins for a particular user
When reviewing the authentication logs the analyst sees the following:
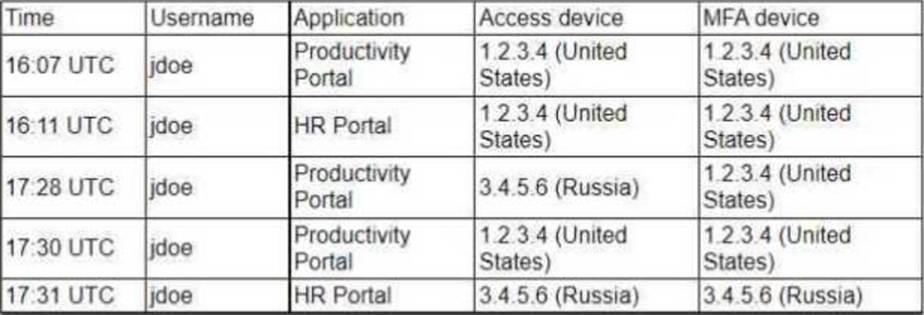
Which of the following are most likely occurring, based on the MFA logs? (Select two).
- A . Dictionary attack
- B . Push phishing
- C . impossible geo-velocity
- D . Subscriber identity module swapping
- E . Rogue access point
- F . Password spray
Which of the following best describes the key goal of the containment stage of an incident response process?
- A . To limit further damage from occurring
- B . To get services back up and running
- C . To communicate goals and objectives of the incident response plan
- D . To prevent data follow-on actions by adversary exfiltration
An organization wants to consolidate a number of security technologies throughout the organization and standardize a workflow for identifying security issues prioritizing the severity and automating a response
Which of the following would best meet the organization’s needs?
- A . MaaS
- B . SIEM
- C . SOAR
- D . CI/CD
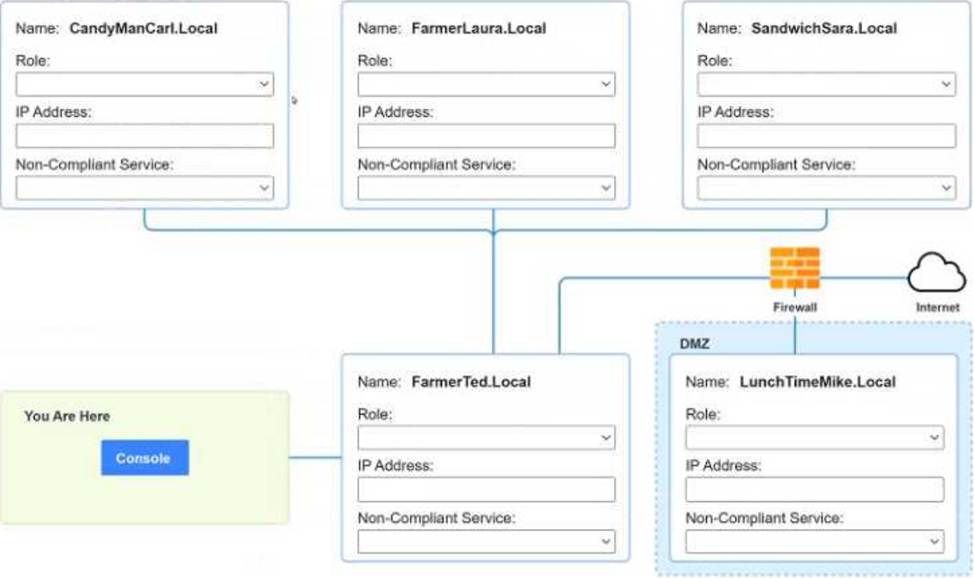
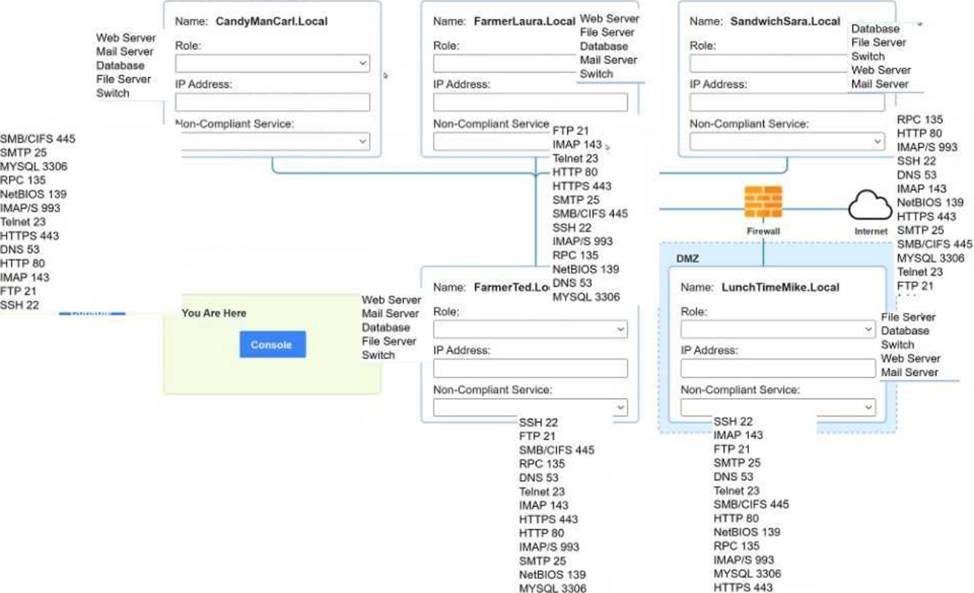
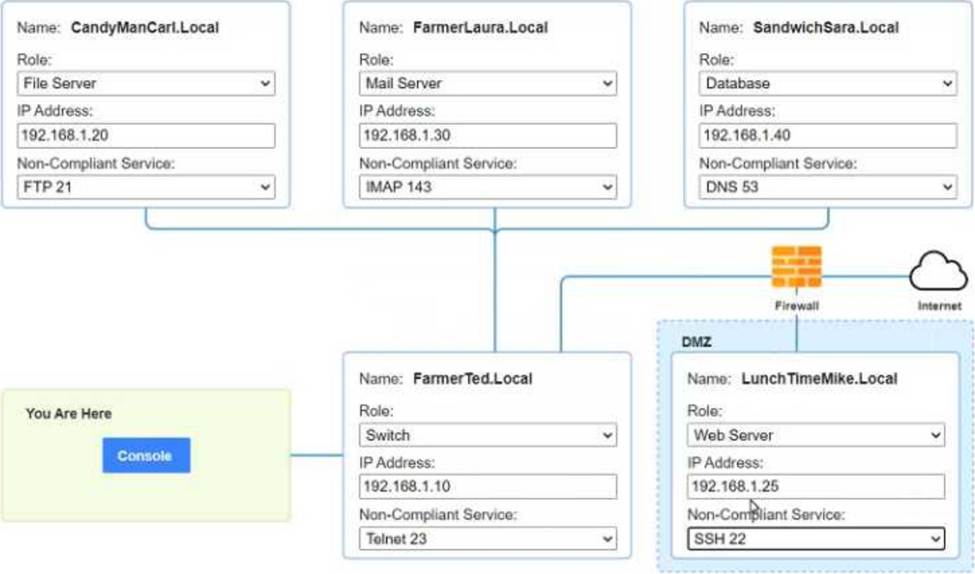
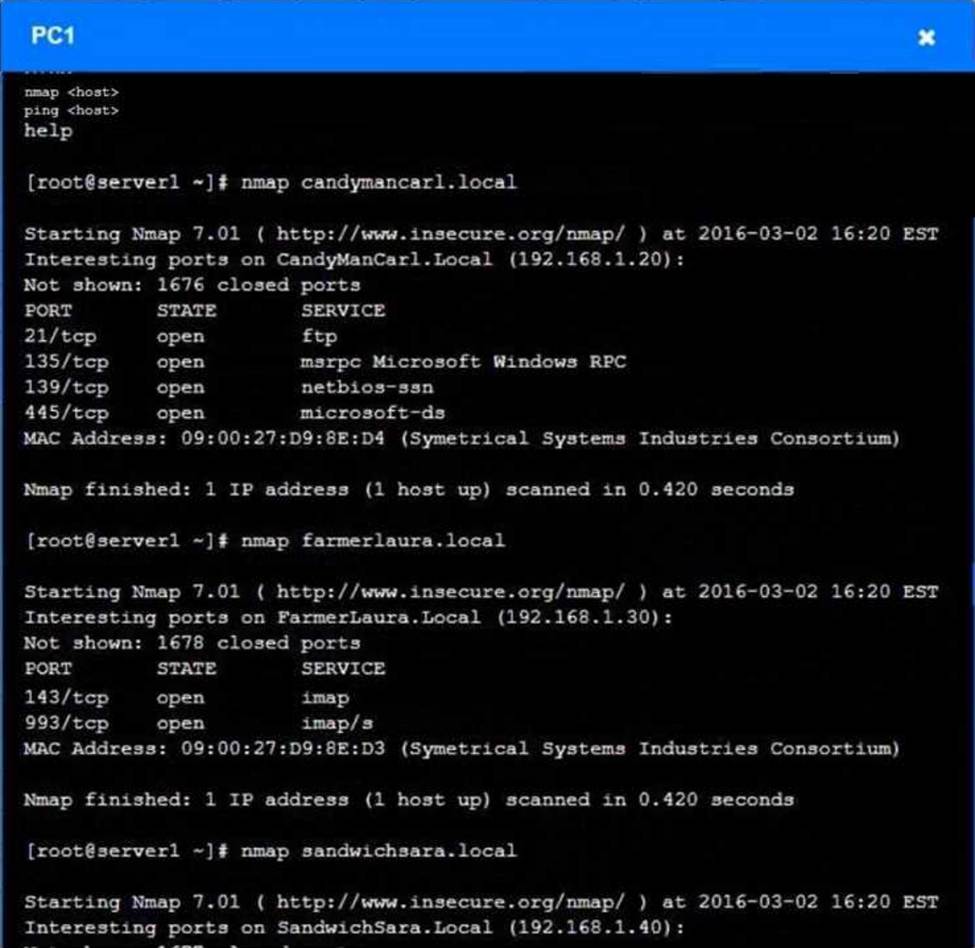
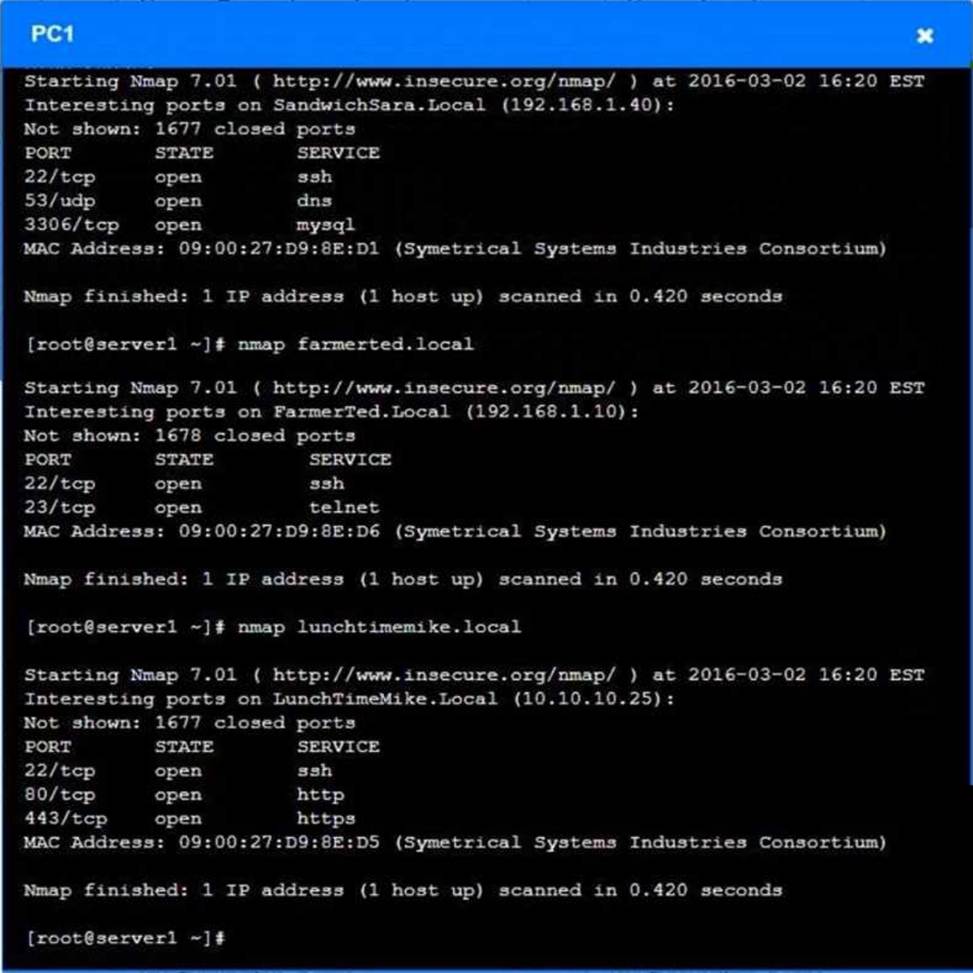
You are a penetration tester who is reviewing the system hardening guidelines for a company.
Hardening guidelines indicate the following.
There must be one primary server or service per device.
Only default port should be used
Non- secure protocols should be disabled.
The corporate internet presence should be placed in a protected subnet
Instructions:
Using the available tools, discover devices on the corporate network and the services running on these devices.
You must determine
ip address of each device
The primary server or service each device
The protocols that should be disabled based on the hardening guidelines