CompTIA CS0-003 Übungsprüfungen
Zuletzt aktualisiert am 28.04.2025- Prüfungscode: CS0-003
- Prüfungsname: CompTIA Cybersecurity Analyst (CySA+) Exam
- Zertifizierungsanbieter: CompTIA
- Zuletzt aktualisiert am: 28.04.2025
An analyst has received an IPS event notification from the SIEM stating an IP address, which is known to be malicious, has attempted to exploit a zero-day vulnerability on several web servers.
The exploit contained the following snippet:
/wp-json/trx_addons/V2/get/sc_layout?sc=wp_insert_user&role=administrator
Which of the following controls would work best to mitigate the attack represented by this snippet?
- A . Limit user creation to administrators only.
- B . Limit layout creation to administrators only.
- C . Set the directory trx_addons to read only for all users.
- D . Set the directory v2 to read only for all users.
A malicious actor has gained access to an internal network by means of social engineering. The actor does not want to lose access in order to continue the attack.
Which of the following best describes the current stage of the Cyber Kill Chain that the threat actor is currently operating in?
- A . Weaponization
- B . Reconnaissance
- C . Delivery
- D . Exploitation
An incident response team finished responding to a significant security incident. The management team has asked the lead analyst to provide an after-action report that includes lessons learned.
Which of the following is the most likely reason to include lessons learned?
- A . To satisfy regulatory requirements for incident reporting
- B . To hold other departments accountable
- C . To identify areas of improvement in the incident response process
- D . To highlight the notable practices of the organization’s incident response team
An organization enabled a SIEM rule to send an alert to a security analyst distribution list when ten failed logins occur within one minute. However, the control was unable to detect an attack with nine failed logins.
Which of the following best represents what occurred?
- A . False positive
- B . True negative
- C . False negative
- D . True positive
During an incident involving phishing, a security analyst needs to find the source of the malicious email.
Which of the following techniques would provide the analyst with this information?
- A . Header analysis
- B . Packet capture
- C . SSL inspection
- D . Reverse engineering
A threat hunter seeks to identify new persistence mechanisms installed in an organization’s environment.
In collecting scheduled tasks from all enterprise workstations, the following host details are aggregated:
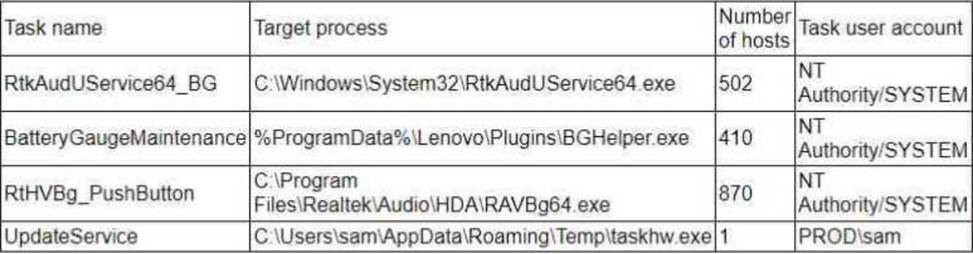
Which of the following actions should the hunter perform first based on the details above?
- A . Acquire a copy of taskhw.exe from the impacted host
- B . Scan the enterprise to identify other systems with taskhw.exe present
- C . Perform a public search for malware reports on taskhw.exe.
- D . Change the account that runs the -caskhw. exe scheduled task
A security analyst needs to provide evidence of regular vulnerability scanning on the company’s network for an auditing process.
Which of the following is an example of a tool that can produce such evidence?
- A . OpenVAS
- B . Burp Suite
- C . Nmap
- D . Wireshark
Which of the following is the greatest security concern regarding ICS?
- A . The involved systems are generally hard to identify.
- B . The systems are configured for automatic updates, leading to device failure.
- C . The systems are oftentimes air gapped, leading to fileless malware attacks.
- D . Issues on the systems cannot be reversed without rebuilding the systems.
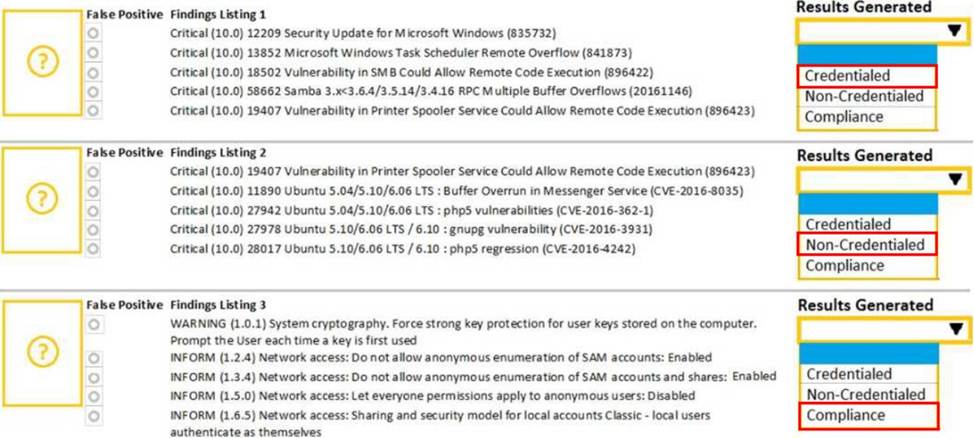
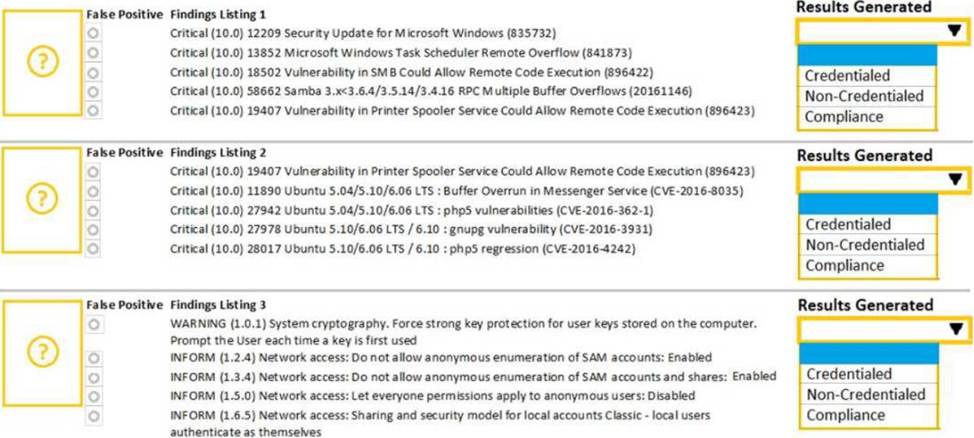
HOTSPOT
A security analyst performs various types of vulnerability scans.
Review the vulnerability scan results to determine the type of scan that was executed and if a false positive occurred for each device. Instructions:
Select the Results Generated drop-down option to determine if the results were generated from a credentialed scan, non-credentialed scan, or a compliance scan.
For ONLY the credentialed and non-credentialed scans, evaluate the results for false positives and check the findings that display false positives. NOTE: If you would like to uncheck an option that is currently selected, click on the option a second time.
Lastly, based on the vulnerability scan results, identify the type of Server by dragging the Server to the results.
The Linux Web Server, File-Print Server and Directory Server are draggable.
If at any time you would like to bring back the initial state of the simulation, please select the Reset All button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
An analyst receives threat intelligence regarding potential attacks from an actor with seemingly unlimited time and resources.
Which of the following best describes the threat actor attributed to the malicious activity?
- A . Insider threat
- B . Ransomware group
- C . Nation-state
- D . Organized crime