CompTIA CV0-004 Übungsprüfungen
Zuletzt aktualisiert am 27.04.2025- Prüfungscode: CV0-004
- Prüfungsname: CompTIA Cloud+ (2024)
- Zertifizierungsanbieter: CompTIA
- Zuletzt aktualisiert am: 27.04.2025
A critical security patch is required on a network load balancer in a public cloud. The organization has a major sales conference next week, and the Chief Executive Officer does not want any interruptions during the demonstration of an application behind the load balancer.
Which of the following approaches should the cloud security engineer take?
- A . Ask the management team to delay the conference.
- B . Apply the security patch after the event.
- C . Ask the upper management team to approve an emergency patch window.
- D . Apply the security patch immediately before the conference.
Users have been reporting that a remotely hosted application is not accessible following a recent migration. However, the cloud administrator is able to access the application from the same site as the users.
Which of the following should the administrator update?
- A . Cipher suite
- B . Network ACL
- C . Routing table
- D . Permissions
An organization needs to retain its data for compliance reasons but only when required.
Which of the following would be the most cost-effective type of tiered storage?
- A . Warm
- B . Hot
- C . Archive
- D . Cold
A cloud consultant needs to modernize a legacy application that can no longer address user demand and is expensive to maintain.
Which of the following is the best migration strategy?
- A . Retain
- B . Rehost
- C . Refactor
- D . Replatform
An administrator received a report that company data has been compromised. The compromise occurred on a holiday, and no one in the organization was working.
While reviewing the logs from the holiday, the administrator noted the following details:
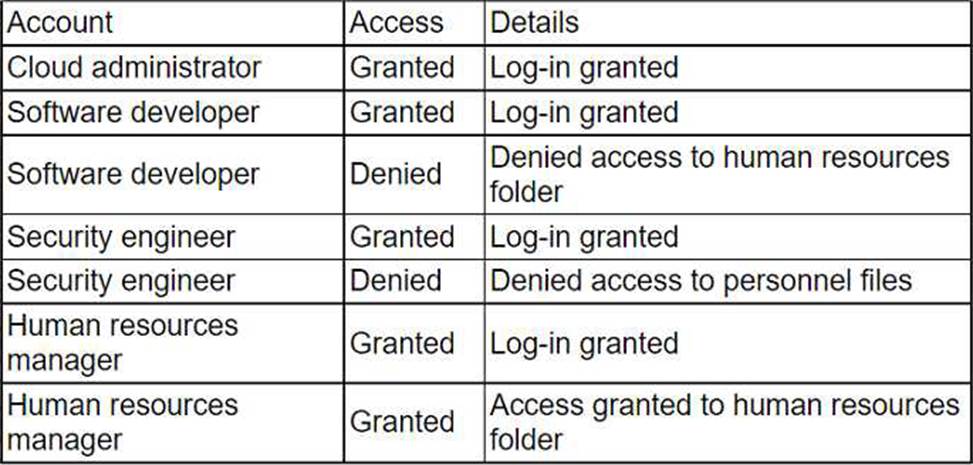
The most appropriate action for the cloud security analyst to recommend is using CIS-hardened images. These images are pre-configured by the Center for Internet Security to provide security benchmark standards that help in mitigating vulnerabilities in publicly available container images.
Reference: CompTIA Cloud+ Study Guide (Exam CV0-004) – Chapter on Cloud Security Posture Which of the following accounts should the administrator disable to prevent a further breach?
- A . Cloud administrator
- B . Human resources manager
- C . Security engineer
- D . Software developer
A security analyst reviews the daily logs and notices the following suspicious activity:
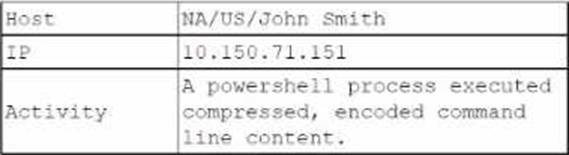
The analyst investigates the firewall logs and identities the following:
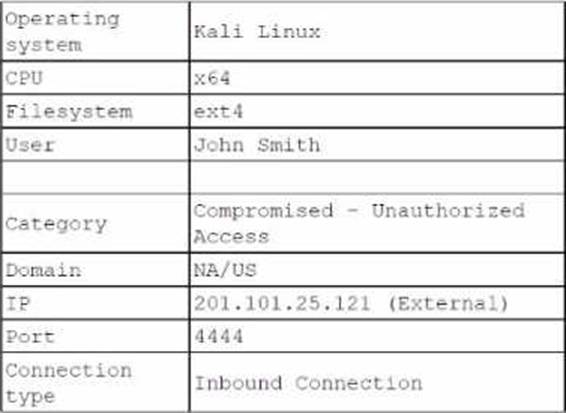
Which of the following steps should the security analyst take next to resolve this issue? (Select two).
- A . Submit an IT support ticket and request Kali Linux be uninstalled from John Smith’s computer
- B . Block all inbound connections on port 4444 and block the IP address 201.101.25.121.
- C . Contact John Smith and request the Ethernet cable attached to the desktop be unplugged
- D . Check the running processes to confirm if a backdoor connection has been established.
- E . Upgrade the Windows x64 operating system on John Smith’s computer to the latest version.
- F . Block all outbound connections from the IP address 10.150.71.151.
An engineer wants lo scale several cloud workloads on demand.
Which of the following approaches is the most suitable?
- A . Load
- B . Scheduled
- C . Manual
- D . Trending
A cloud engineer hardened the WAF for a company that operates exclusively in North America. The engineer did not make changes to any ports, and all protected applications have continued to function as expected.
Which of the following configuration changes did the engineer most likely apply?
- A . The engineer implemented MFA to access the WAF configurations.
- B . The engineer blocked all traffic originating outside the region.
- C . The engineer installed the latest security patches on the WAF.
- D . The engineer completed an upgrade from TLS version 1.1 to version 1.3.
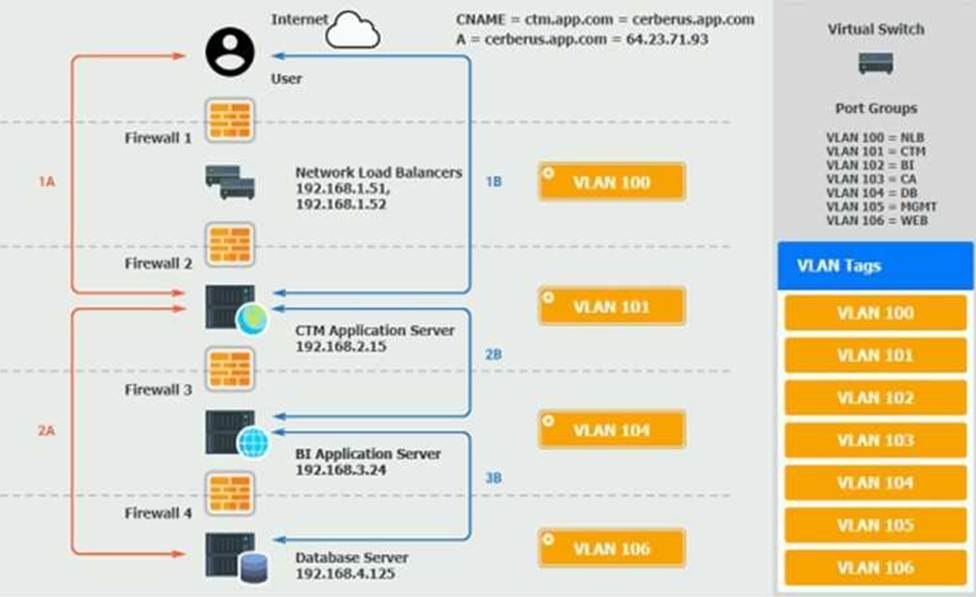
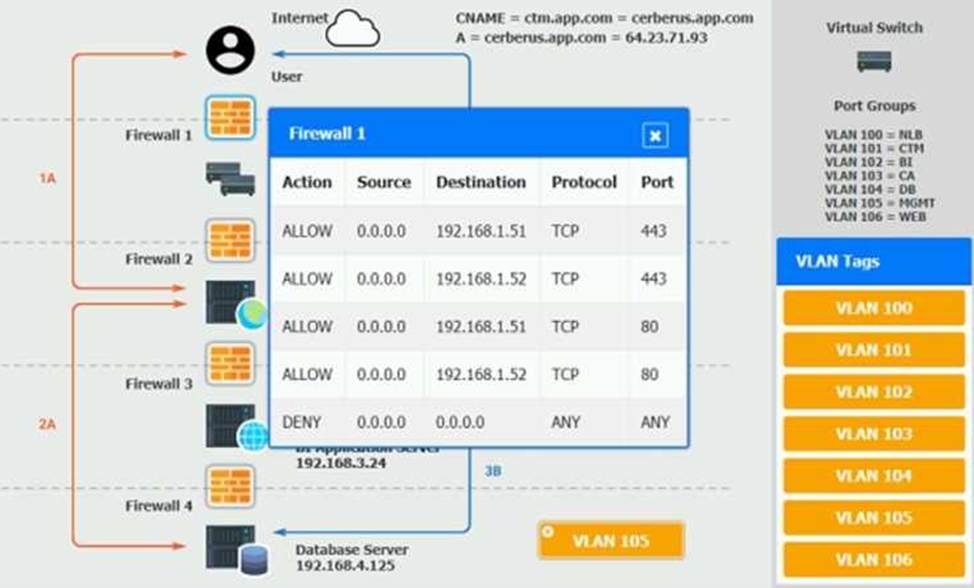
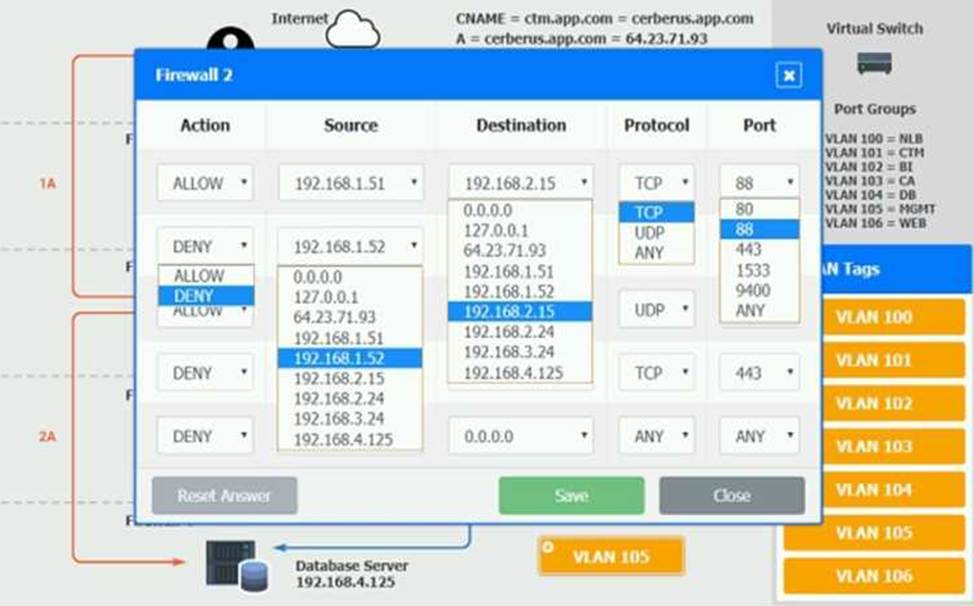
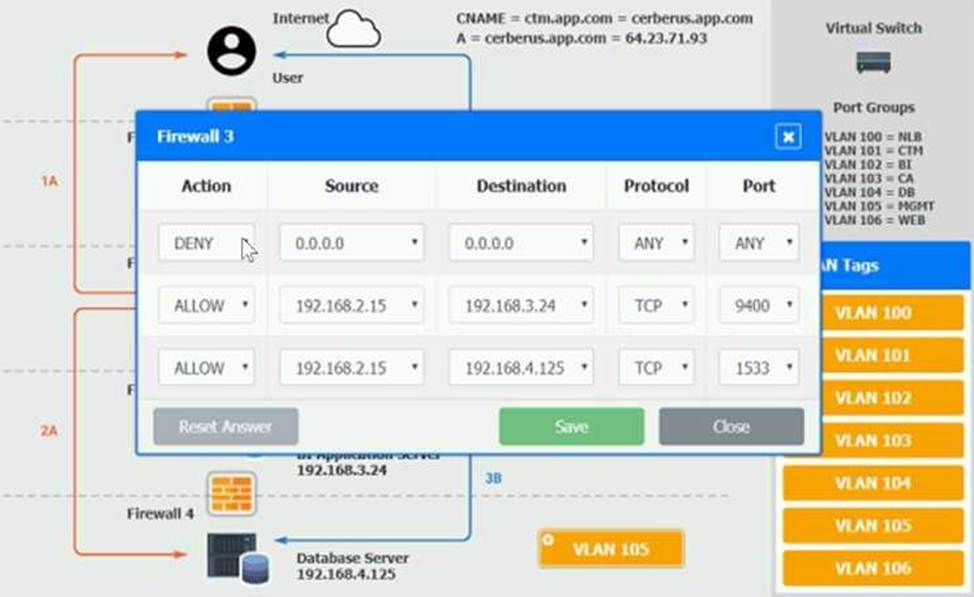
The QA team is testing a newly implemented clinical trial management (CTM) SaaS application that uses a business intelligence application for reporting. The UAT users were instructed to use HTTP and HTTPS.
Refer to the application dataflow:
1A C The end user accesses the application through a web browser to enter and view clinical data.
2A C The CTM application server reads/writes data to/from the database server.
1B C The end user accesses the application through a web browser to run reports on clinical data.
2B C The CTM application server makes a SOAP call on a non-privileged port to the BI application server.
3B C The BI application server gets the data from the database server and presents it to the CTM application server.
When UAT users try to access the application using https://ctm.app.com or http://ctm.app.com, they get a message stating: “Browser cannot display the webpage.” The QA team has raised a ticket to troubleshoot the issue.
INSTRUCTIONS
You are a cloud engineer who is tasked with reviewing the firewall rules as well as virtual network settings.
You should ensure the firewall rules are allowing only the traffic based on the dataflow.
You have already verified the external DNS resolution and NAT are working.
Verify and appropriately configure the VLAN assignments and ACLs. Drag and drop the appropriate VLANs to each tier from the VLAN Tags table. Click on each Firewall to change ACLs as needed.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.

A developer is building a new application version using a CI/CD pipeline.
The developer receives the following error message log when the build fails:
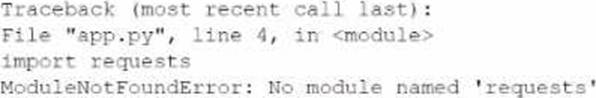
Which of the following is the most likely cause of this failure?
- A . Incorrect version
- B . Test case failure
- C . Broken build pipeline
- D . Dependency issue
