CompTIA CV0-004 Übungsprüfungen
Zuletzt aktualisiert am 28.04.2025- Prüfungscode: CV0-004
- Prüfungsname: CompTIA Cloud+ (2024)
- Zertifizierungsanbieter: CompTIA
- Zuletzt aktualisiert am: 28.04.2025
A company needs to deploy its own code directly in the cloud without provisioning additional infrastructure.
Which of the following is the best cloud service model for the company to use?
- A . PaaS
- B . SaaS
- C . laaS
- D . XaaS
For compliance purposes, a cloud developer at an insurance company needs to save all customer policies for more than ten years.
Which of the following options is the most cost-efficient tier to save the data in the cloud?
- A . Archive
- B . Hot
- C . Cold
- D . Warm
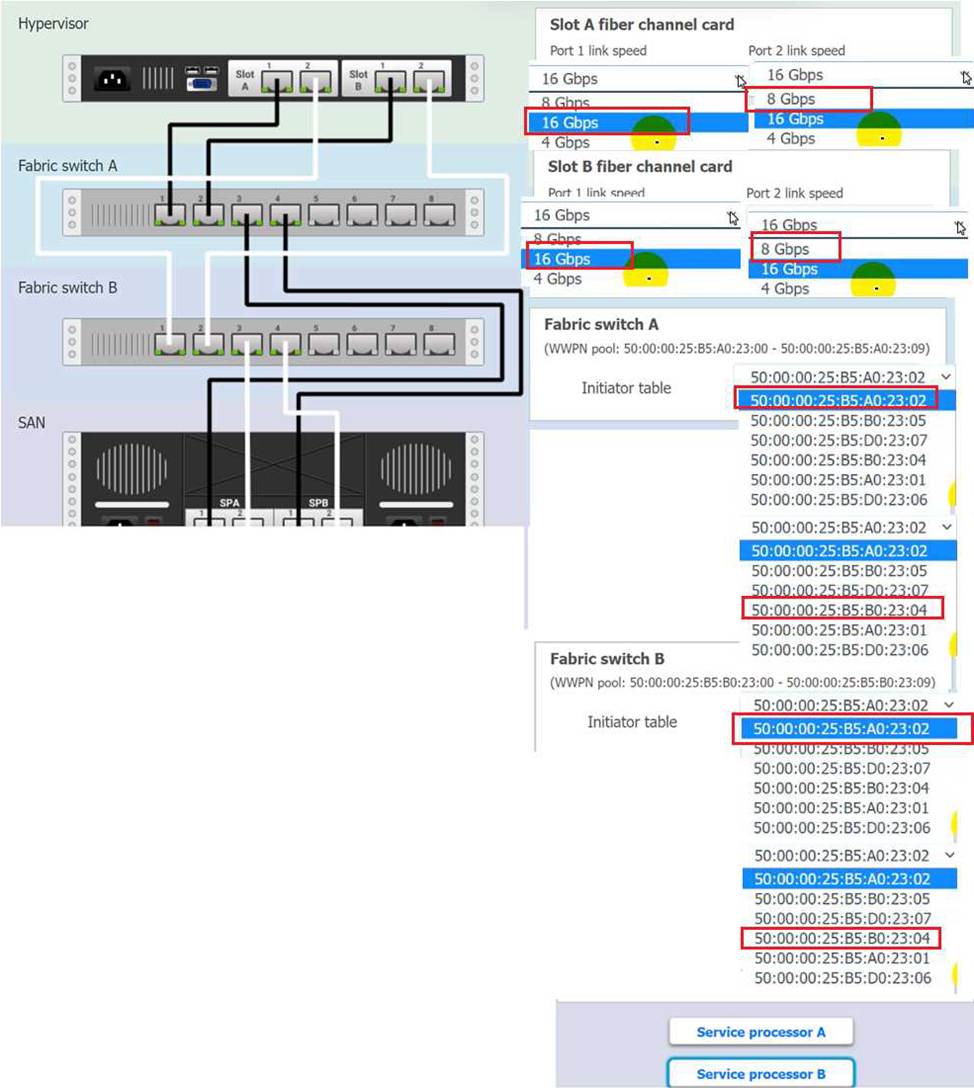
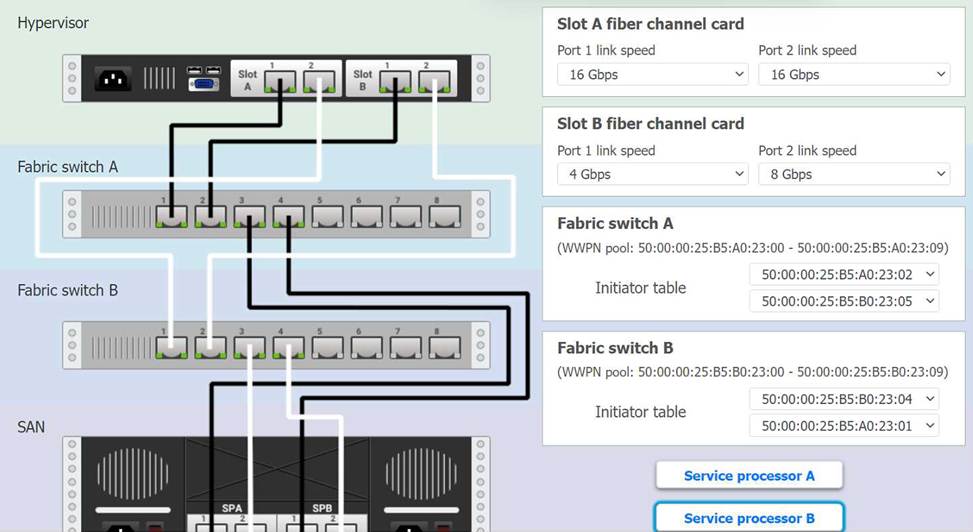
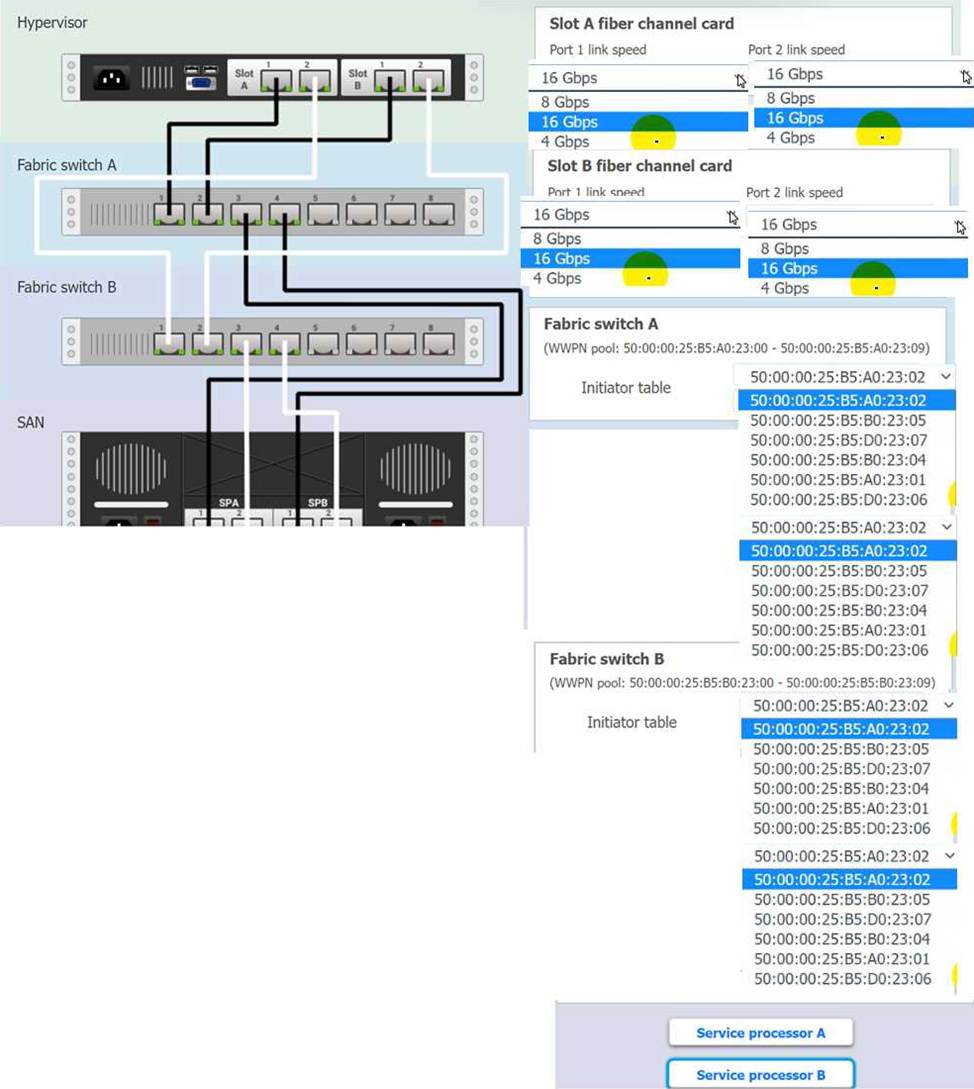
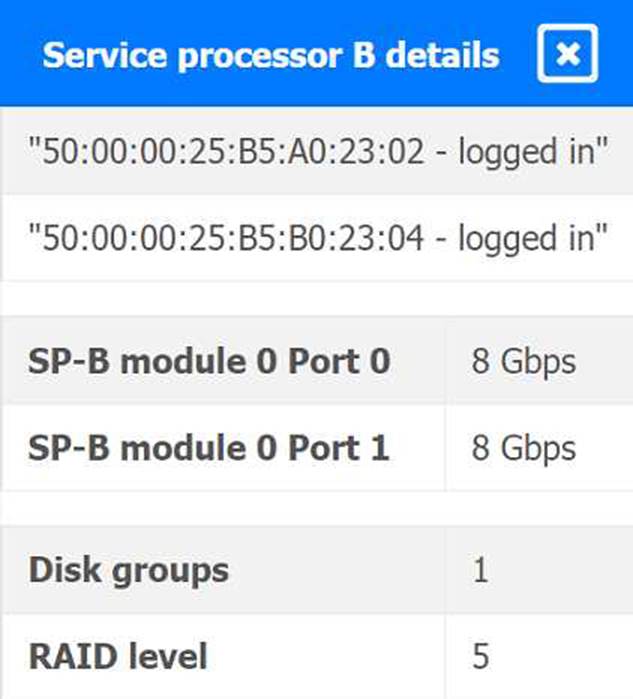
You are a cloud engineer working for a cloud service provider that is responsible for an IaaS offering.
Your customer, who creates VMs and manages virtual storage, has noticed I/O bandwidth issues and low IOPS (under 9000).
Your manager wants you to verify the proper storage configuration as dictated by your service level agreement (SLA).
The SLA specifies:
. Each SFP on the hypervisor host must be set to the maximum link speed
allowed by the SAN array. . All SAN array disk groups must be configured in a RAID 5.
. The SAN array must be fully configured for redundant fabric paths. . IOPS should not fall below 14000
INSTRUCTIONS
Click on each service processor to review the displayed information. Then click on the drop-down menus to change the settings of each device as necessary to conform to the SLA requirements.

An organization is hosting a seminar with eight individuals who need to connect to their own dedicated VM.
The technician used the following VM configurations:
IP address: DHCP
NIC: 1Gbps
Network: 10.1.10.0/29
Several users are unable to access their VMs.
Which of the following best describes the reason?
- A . Not enough addresses are available.
- B . The routes are misconfigured.
- C . Too much traffic is on the network.
- D . DHCP is not working correctly on the VM.
A security engineer Identifies a vulnerability m a containerized application. The vulnerability can be exploited by a privileged process to read tie content of the host’s memory.
The security engineer reviews the following Dockerfile to determine a solution to mitigate similar exploits:
![]()
Which of the following is the best solution to prevent similar exploits by privileged processes?
- A . Adding the USER myappuserinstruction
- B . Patching the host running the Docker daemon
- C . Changing FROM alpiner3.17 to FROM alpine:latest
- D . Running the container with the ready-only filesystem configuration
A cloud engineer is provisioning a new application that requires access to the organization’s public cloud resources.
Which of the following is the best way for the cloud engineer to authenticate the application?
- A . Access key
- B . API
- C . MFA token
- D . Username and Password
A company wants to build its new platform using a public cloud.
The workload requirements include the following:
• Implementation of custom CIS compliance
• Patch for vulnerabilities within 24 hours
• Warrant at least 1,800 IOPS per volume
Which of the following meets the requirements?
- A . SaaS
- B . laaS
- C . FaaS
- D . PaaS
A customer is migrating applications to the cloud and wants to grant authorization based on the classification levels of each system.
Which of the following should the customer implement to ensure authorisation to systems is granted when the user and system classification properties match? (Select two).
- A . Resource tagging
- B . Discretionary access control
- C . Multifactor authentication
- D . Role-based access control
- E . Token-based authentication
- F . Bastion host
A manager wants information about which users signed in to a certain VM during the past month.
Which of the following can the cloud administrator use to obtain this information?
- A . Retention
- B . Alerting
- C . Aggregation
- D . Collection
A systems administrator is provisioning VMs according to the following requirements:
・ A VM instance needs to be present in at least two data centers.
. During replication, the application hosted on the VM tolerates a maximum latency of one second.
・ When a VM is unavailable, failover must be immediate.
Which of the following replication methods will best meet these requirements?
- A . Snapshot
- B . Transactional
- C . Live
- D . Point-in-time