DELL EMC D-CSF-SC-01 Übungsprüfungen
Zuletzt aktualisiert am 27.04.2025- Prüfungscode: D-CSF-SC-01
- Prüfungsname: Dell NIST Cybersecurity Framework 2.0
- Zertifizierungsanbieter: DELL EMC
- Zuletzt aktualisiert am: 27.04.2025
An organization is creating a customized version of the NIST Cybersecurity Framework to align with its unique risk profile and business requirements. They are currently mapping their organizational priorities and risk tolerance to the framework functions.
Which part of the NIST Framework are they focusing on?
- A . Core
- B . Tiers
- C . Profiles
- D . Objectives
Consider the following situation:
– A complete service outage has occurred, affecting critical services
– Users are unable to perform their tasks
– Customers are unable to conduct business
– Financial impact is beyond the highest allowed threshold
What is the correct classification level for this situation?
- A . Safety critical
- B . Mission critical
- C . Business critical
- D . High impact
What is the purpose of the Asset Management category?
- A . Prevent unauthorized access, damage, and interference to business premises and information
- B . Support asset management strategy and information infrastructure security policies
- C . Avoid breaches of any criminal or civil law, statutory, regulatory, or contractual obligations
- D . Inventory physical devices and systems, software platform and applications, and communication flows
The ___ profile in the NIST Cybersecurity Framework represents the desired cybersecurity outcomes aligned with the organization’s risk tolerance.
- A . Current
- B . Target
- C . Risk
- D . Maturity
When should event analysis be performed?
- A . Only when requested by an auditor
- B . Routinely for all events collected on a mission critical system
- C . Only at the discretion of an authorized security analyst
- D . After an event is triggered by the detection system
Refer to the exhibit.
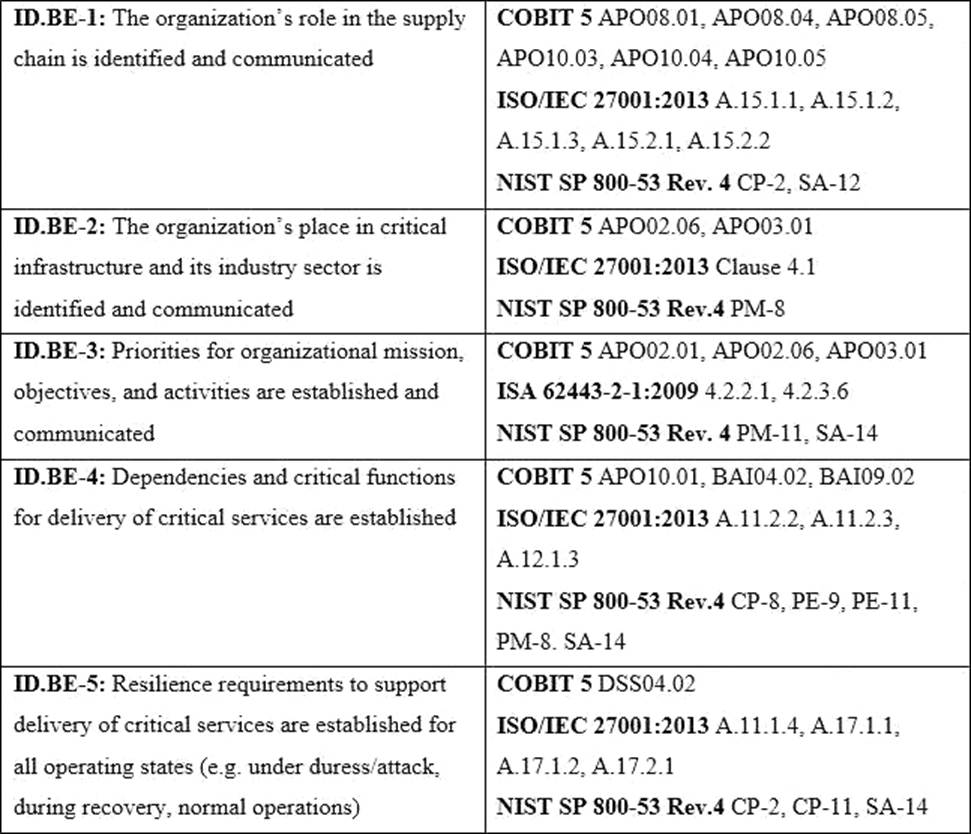
What type of item appears in the second column of the table?
- A . Subcategory
- B . Informative Reference
- C . Function
- D . Tier
An Internet-connected file server compromised by a threat that leaked all data. The data was destroyed to cover all tracks. The file server has high availability capabilities to handle critical workloads. The operations team took only 15 minutes to restore workload routing to a different node.
What part(s) of the CIA Triad was affected?
- A . A only
- B . C, I
- C . C, A
- D . A, I
In the context of the Respond Function, which actions are taken to contain a security incident? (Select two)
- A . Isolating affected systems
- B . Updating access control lists
- C . Performing root cause analysis
- D . Notifying stakeholders
What is a result of an incomplete organizational asset identification process?
- A . Vendors will not receive payment from the organization
- B . Purchases will be delayed by the organization
- C . Risk will be introduced into the organization
- D . System disruptions will have less impact on the organization
What is a result of an incomplete organizational asset identification process?
- A . Vendors will not receive payment from the organization
- B . Purchases will be delayed by the organization
- C . Risk will be introduced into the organization
- D . System disruptions will have less impact on the organization
