DELL EMC D-DP-FN-01 Übungsprüfungen
Zuletzt aktualisiert am 24.04.2025- Prüfungscode: D-DP-FN-01
- Prüfungsname: Dell Data Protection Management Foundations v2 Exam
- Zertifizierungsanbieter: DELL EMC
- Zuletzt aktualisiert am: 24.04.2025
Which is a feature of Software Defined Data Center?
- A . Metering
- B . Monitoring
- C . Erasure coding
- D . Security hardening
What is a challenge when implementing data protection in hybrid environments?
- A . Inconsistent encryption standards
- B . Ensuring data consistency across platforms
- C . Limited backup scheduling options
- D . High power consumption of servers
Which combination forms a data lake?
- A . MongoDB and MariaDB
- B . HDFS and Hadoop
- C . MariaDB and Oracle
- D . Hadoop and NoSQL
What does the Software Defined Data Center controller provide?
- A . Storage external to the controller to request resources
- B . Rapid provisioning of resources based on pre-defined policies
- C . Load balancing that enables only cloud applications external to the controller to request resources
- D . Interfaces that enable only cloud applications external to the controller to request resources
What does the Software Defined Data Center controller provide?
- A . Storage external to the controller to request resources
- B . Rapid provisioning of resources based on pre-defined policies
- C . Load balancing that enables only cloud applications external to the controller to request resources
- D . Interfaces that enable only cloud applications external to the controller to request resources
Which disaster recovery test is most comprehensive?
- A . Tabletop exercise
- B . Simulation testing
- C . Full-scale recovery testing
- D . Partial workload testing
What is a primary feature of modern automated backup tools?
- A . Manual intervention required
- B . Integration with hybrid cloud environments
- C . Incompatibility with virtualization
- D . Limited encryption capabilities
Refer to the exhibit.
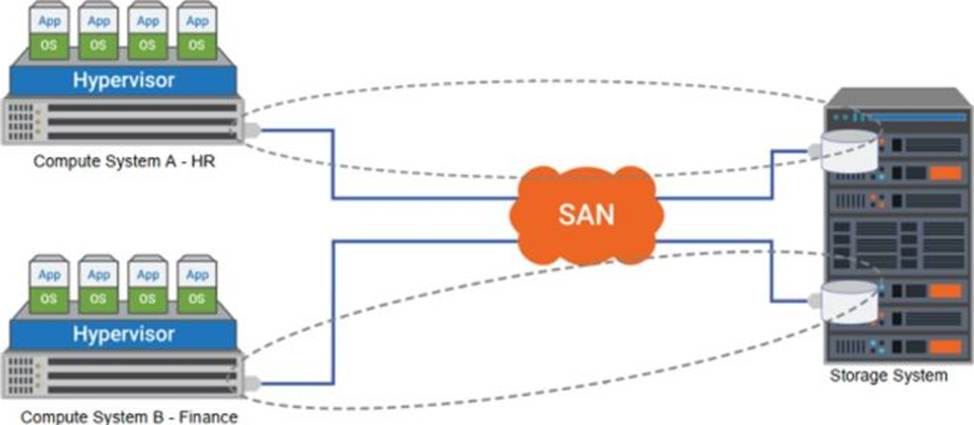
A company stores data from two different departments on one disk array. Each department can access and modify data from the other department.
Which security control will prevent the departments from seeing each other’s data?
- A . Zoning
- B . Shadow copy
- C . VPN
- D . LUN masking
A computer has an MTBF of 11000 hours and an MTTR of 15 hours?
What is the availability of the data?
- A . 90.00%
- B . 98.91%
- C . 99.52%
- D . 99.86%
What are the key approaches to application transformation?
- A . Restore, Reuse, Retain, Retire
- B . Refactor, Revise, Retain, Retire
- C . Retain, Refactor, Reuse, Revise
- D . Revise, Restore, Retain, Re-iterate
