DELL EMC D-ISM-FN-23 Übungsprüfungen
Zuletzt aktualisiert am 27.04.2025- Prüfungscode: D-ISM-FN-23
- Prüfungsname: Dell Information Storage and Management Foundations 2023
- Zertifizierungsanbieter: DELL EMC
- Zuletzt aktualisiert am: 27.04.2025
A customer wants 24×7 availability for a business application that uses a file system.
Which operation ensures a consistent replica of the file system?
- A . Unmount the file system prior to the creation of the replica
- B . Stop the application prior to the creation of the replica
- C . Flush the file system buffers after creation of the replica
- D . Flush the file system buffers before creation of the replica
Magnetic tape drive
Description:
A) Stores data on a circular disk with a ferromagnetic coating
B) Stores data on semiconductor-based memory
C) Stores data on a thin plastic film with a magnetic coating
D) Stores data on a polycarbonate disc with a reflective coating
- A . 1-B, 2-D, 3-A, 4-C
- B . 1-A, 2-D, 3-B, 4-C
- C . 1-C, 2-B, 3-A, 4-D
- D . 1-D, 2-C, 3-B, 4-A
Which technique prevents compute systems from gaining unauthorized access to storage volumes in a shared storage environment?
- A . Fabric binding
- B . Zoning
- C . Concatenating metaLUNs
- D . LUN masking
A backup administrator has defined a backup policy. The policy requires full backups to be performed at 9 PM every Sunday and incremental backups performed at 9 PM the remaining days.
If files were accidentally deleted Thursday morning, how many backup copies are required to restore the files?
- A . 3
- B . 5
- C . 4
- D . 2
What is an accurate statement about Challenge Handshake Authentication Protocol (CHAP) control?
- A . Enables initiators and targets to authenticate each other by using a shared secret code
- B . Provides strong authentication for client-server applications by using secret-key cryptography
- C . Allows a client to access protected resources from a resource server on behalf of a resource owner
- D . Enables an organization to use authentication services from an identity provider
What is an advantage of the changed block tracking backup technique?
- A . Reduces the backup window
- B . Enables restoration to any point-in-time
- C . Eliminates the need for data deduplication
- D . Increases backup device performance
Which compute system component enables dynamic extension of file system capacity and efficient storage management?
- A . Logical Unit Number
- B . Logical Unit Number Masking
- C . Logical Volume Manager
- D . Virtual Memory Manager
Based on the exhibit, what does the "X", "Y", and "Z" represent in a NAS environment?
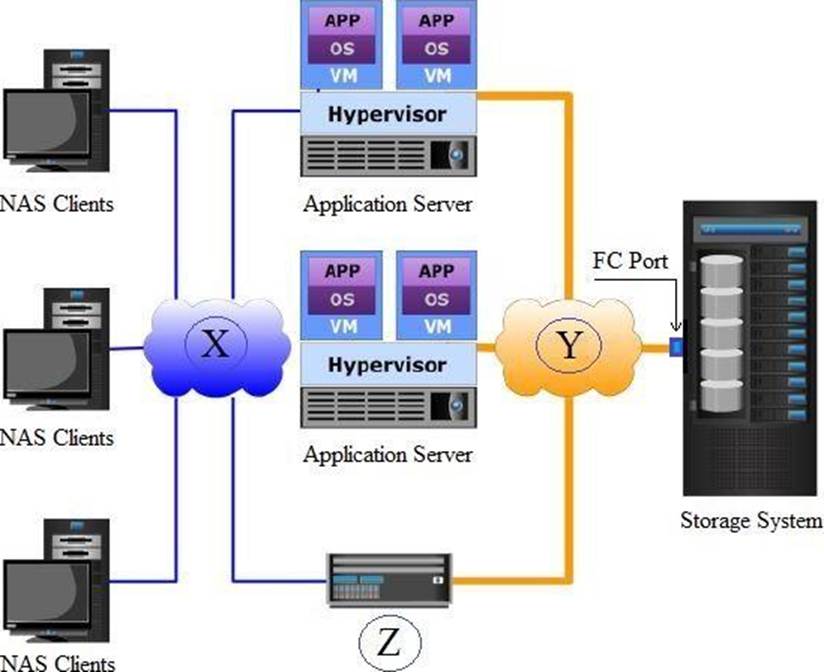
- A . X = FC SAN, Y = IP Network, and Z = NAS Gateway
- B . X = IP Network, Y = FC SAN, and Z = NAS Gateway
- C . X = FC SAN, Y = NAS Gateway, and Z= IP Network
- D . X = IP Network, Y = NAS Gateway, and Z = FC SAN
What is a key advantage of NVMe over Fabrics?
- A . Reducing the effectiveness of storage
- B . Providing higher latency than traditional storage protocols
- C . Providing lower latency and higher performance
- D . Reducing network reliability
What is an activity in the risk assessment step of risk management?
- A . Determine the likelihood of a risk
- B . Plan and deploy security controls
- C . Continuously observe the existing risks
- D . Identify the sources of threats that increase the risks
