Fortinet FCP_FCT_AD-7.2 Übungsprüfungen
Zuletzt aktualisiert am 26.04.2025- Prüfungscode: FCP_FCT_AD-7.2
- Prüfungsname: FCP - FortiClient EMS 7.2 Administrator
- Zertifizierungsanbieter: Fortinet
- Zuletzt aktualisiert am: 26.04.2025
By default, what happens when a log file reaches its maximum file size?
- A . FortiAnalyzer overwrites the log files.
- B . FortiAnalyzer stops logging.
- C . FortiAnalyzer rolls the active log by renaming the file.
- D . FortiAnalyzer forwards logs to syslog.
By default, what happens when a log file reaches its maximum file size?
- A . FortiAnalyzer overwrites the log files.
- B . FortiAnalyzer stops logging.
- C . FortiAnalyzer rolls the active log by renaming the file.
- D . FortiAnalyzer forwards logs to syslog.
By default, what happens when a log file reaches its maximum file size?
- A . FortiAnalyzer overwrites the log files.
- B . FortiAnalyzer stops logging.
- C . FortiAnalyzer rolls the active log by renaming the file.
- D . FortiAnalyzer forwards logs to syslog.
An administrator installs FortiClient EMS in the enterprise.
Which component is responsible for enforcing protection and checking security posture?
- A . FortiClient EMS tags
- B . FortiClient vulnerability scan
- C . FortiClient
- D . FortiClient EMS
An administrator installs FortiClient EMS in the enterprise.
Which component is responsible for enforcing protection and checking security posture?
- A . FortiClient EMS tags
- B . FortiClient vulnerability scan
- C . FortiClient
- D . FortiClient EMS
Refer to the exhibits.
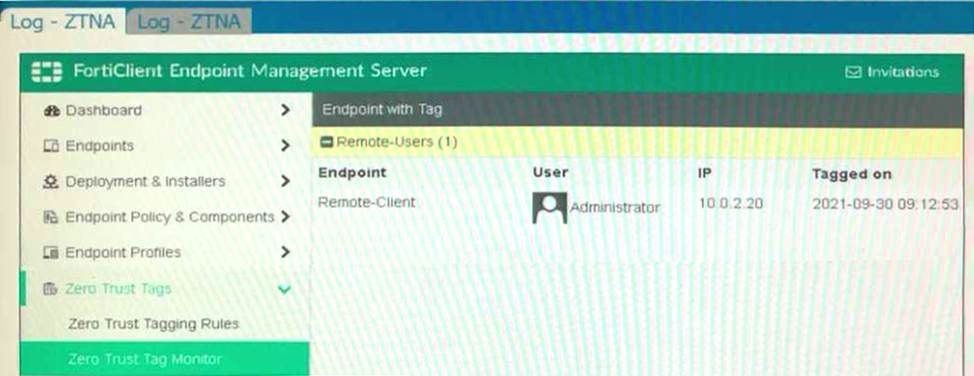
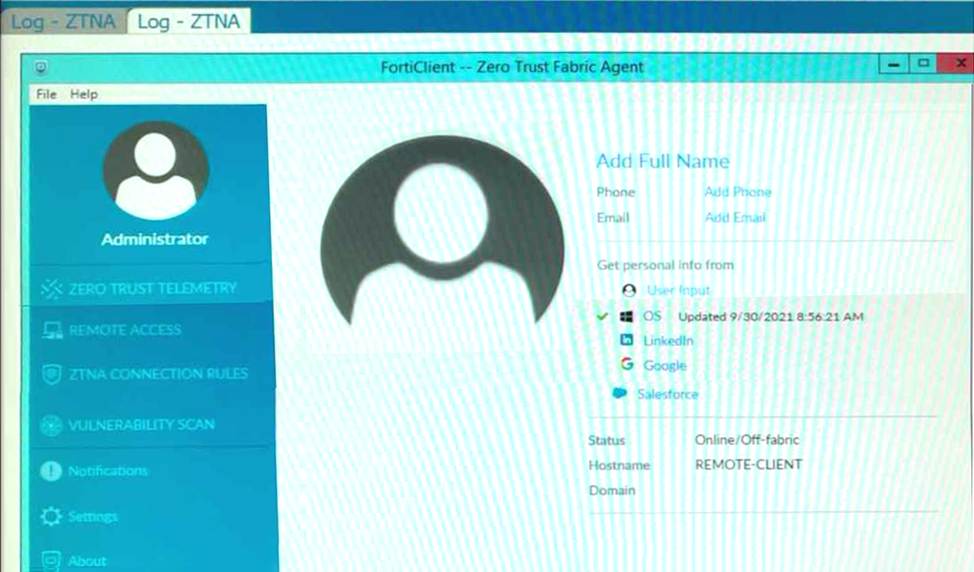
Which show the Zero Trust Tag Monitor and the FortiClient GUI status.
Remote-Client is tagged as Remote-Users on the FortiClient EMS Zero Trust Tag Monitor.
What must an administrator do to show the tag on the FortiClient GUI?
- A . Update tagging rule logic to enable tag visibility
- B . Change the FortiClient system settings to enable tag visibility
- C . Change the endpoint control setting to enable tag visibility
- D . Change the user identity settings to enable tag visibility
An administrator configures ZTNA configuration on the FortiGate.
Which statement is true about the firewall policy?
- A . It redirects the client request to the access proxy.
- B . It uses the access proxy.
- C . It defines ZTNA server.
- D . It only uses ZTNA tags to control access for endpoints.
An administrator deploys a FortiClient installation through the Microsoft AD group policy After installation is complete all the custom configuration is missing.
What could have caused this problem?
- A . The FortiClient exe file is included in the distribution package
- B . The FortiClient MST file is missing from the distribution package
- C . FortiClient does not have permission to access the distribution package.
- D . The FortiClient package is not assigned to the group
Refer to the exhibit.
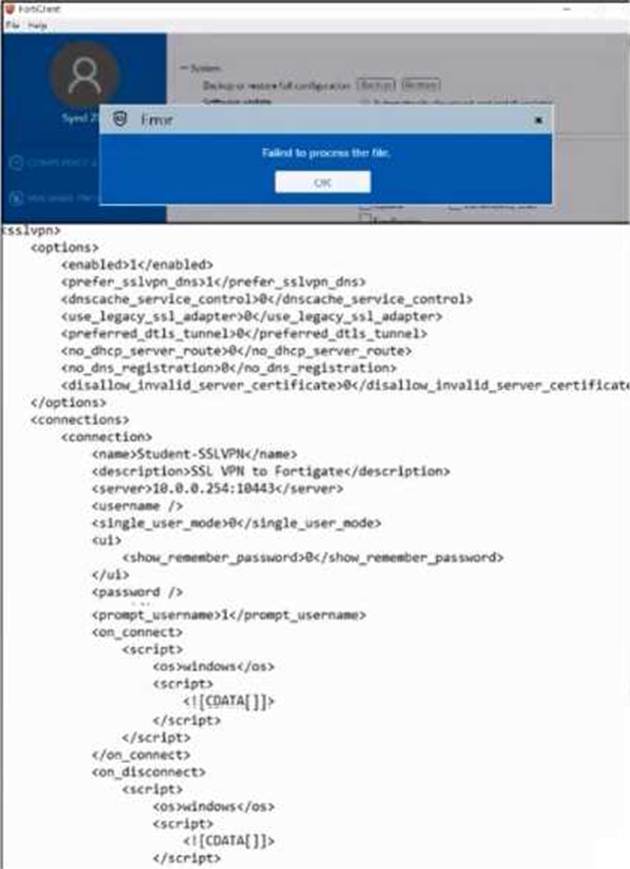
An administrator has restored the modified XML configuration file to FortiClient and sees the error shown in the exhibit.
Based on the XML settings shown in the exhibit, what must the administrator do to resolve the issue with the XML configuration file?
- A . The administrator must resolve the XML syntax error.
- B . The administrator must use a password to decrypt the file
- C . The administrator must change the file size
- D . The administrator must save the file as FortiClient-config conf.
An administrator wants to simplify remote access without asking users to provide user credentials.
Which access control method provides this solution?
- A . ZTNA full mode
- B . SSL VPN
- C . L2TP
- D . ZTNA IP/MAC littering mode
