Fortinet FCP_FCT_AD-7.2 Übungsprüfungen
Zuletzt aktualisiert am 26.04.2025- Prüfungscode: FCP_FCT_AD-7.2
- Prüfungsname: FCP - FortiClient EMS 7.2 Administrator
- Zertifizierungsanbieter: Fortinet
- Zuletzt aktualisiert am: 26.04.2025
ZTNA Network Topology
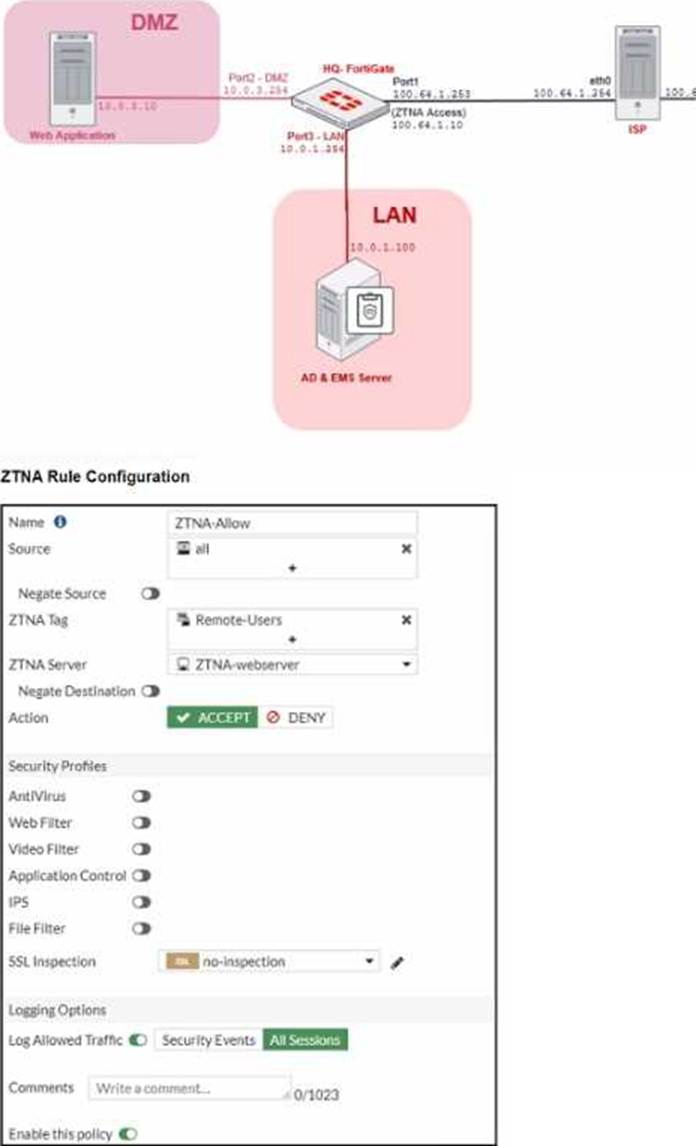
Refer to the exhibits, which show a network topology diagram of ZTNA proxy access and the ZTNA rule configuration.
An administrator runs the diagnose endpoint record list CLI command on FortiGate to check Remote-Client endpoint information, however Remote-Client is not showing up in the endpoint record list.
What is the cause of this issue?
- A . Remote-Client has not initiated a connection to the ZTNA access proxy.
- B . Remote-Client provided an empty client certificate to connect to the ZTNA access proxy.
- C . Remote-Client provided an invalid certificate to connect to the ZTNA access proxy.
- D . Remote-Client failed the client certificate authentication.
Refer to the exhibit.
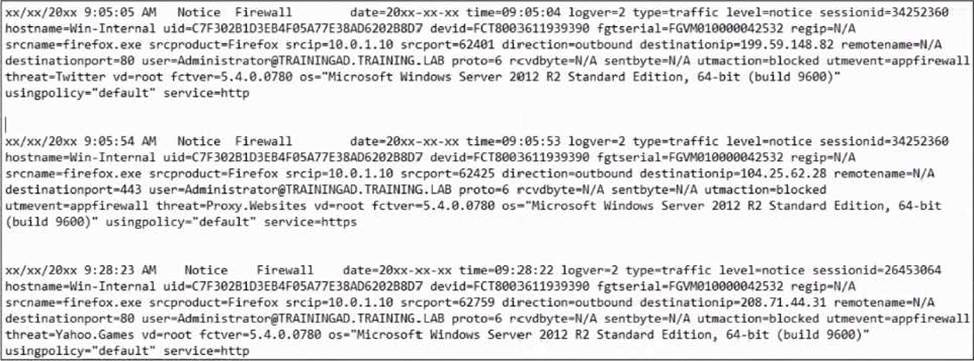
Based on the FortiClient logs shown in the exhibit which application is blocked by the application firewall?
- A . Twitter
- B . Facebook
- C . Internet Explorer
- D . Firefox
What action does FortiClient anti-exploit detection take when it detects exploits?
- A . Deletes the compromised application process
- B . Patches the compromised application process
- C . Blocks memory allocation to the compromised application process
- D . Terminates the compromised application process
FortiClient EMS endpoint policies
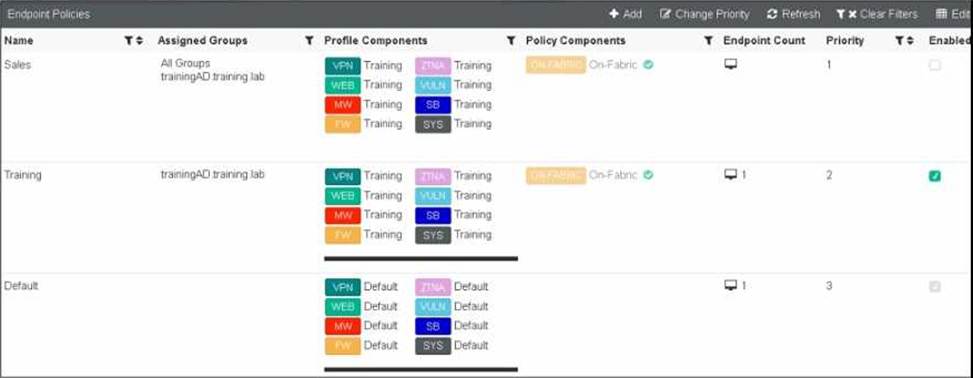
Refer to the exhibit, which shows multiple endpoint policies on FortiClient EMS.
Which policy is applied to the endpoint in the AD group trainingAD
- A . The Training policy
- B . Both the Sales and Training policies because their priority is higher than the Default policy
- C . The Default policy because it has the highest priority
- D . The sales policy
An administrator is required to maintain a software vulnerability on the endpoints, without showing the feature on the FortiClient.
What must the administrator do to achieve this requirement?
- A . Select the vulnerability scan feature in the deployment package, but disable the feature on the endpoint profile
- B . Disable select the vulnerability scan feature in the deployment package
- C . Click the hide icon on the vulnerability scan profile assigned to endpoint
- D . Use the default endpoint profile
Refer to the exhibit.
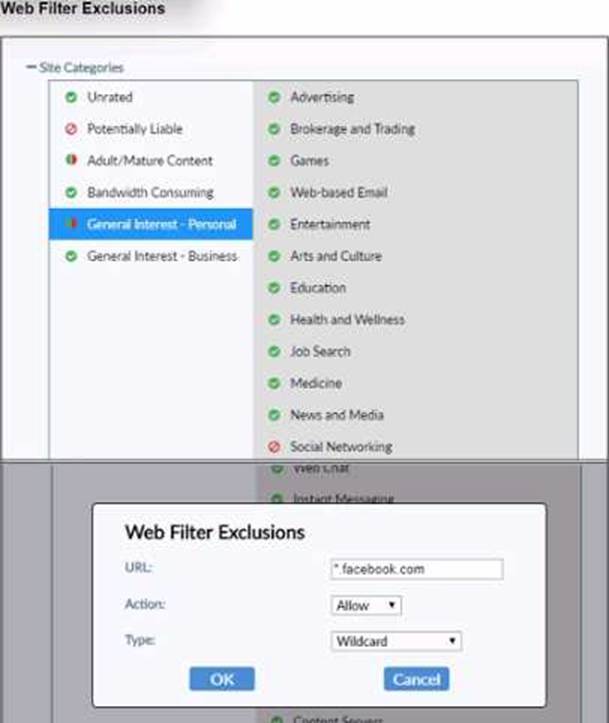
Based on the settings shown in the exhibit, which action will FortiClient take when users try to access www.facebook.com?
- A . FortiClient will allow access to Facebook.
- B . FortiClient will block access to Facebook and its subdomains.
- C . FortiClient will monitor only the user’s web access to the Facebook website
- D . FortiClient will prompt a warning message to want the user before they can access the Facebook website
When site categories are disabled in FortiClient web filter, which feature can be used to protect the endpoint from malicious web access?
- A . Real-time protection list
- B . Block malicious websites on antivirus
- C . FortiSandbox URL list
- D . Web exclusion list
Which statement about the FortiClient enterprise management server is true?
- A . It receives the configuration information of endpoints from ForuGate.
- B . It provides centralized management of multiple endpoints running FortiClient software.
- C . It enforces compliance on the endpoints using tags
- D . It receives the CA certificate from FortiGate to validate client certrficates.
Which three types of antivirus scans are available on FortiClient? (Choose three)
- A . Proxy scan
- B . Full scan
- C . Custom scan
- D . Flow scan
- E . Quick scan
Refer to the exhibit.
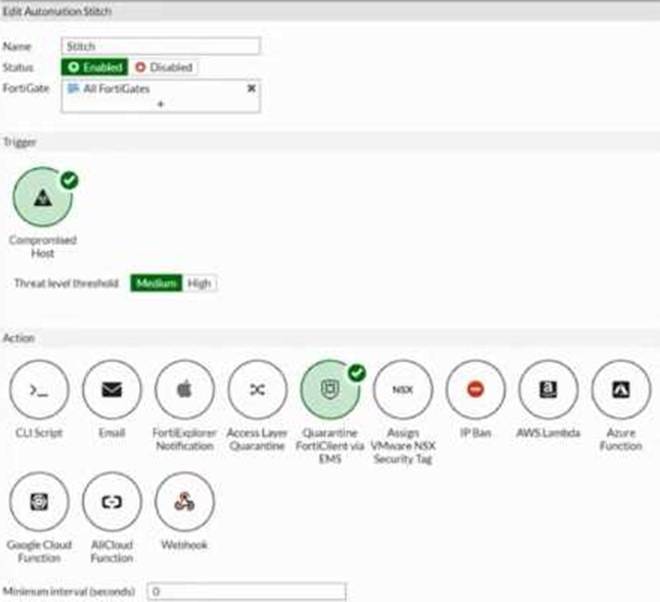
Based on the Security Fabric automation settings, what action will be taken on compromised endpoints?
- A . Endpoints will be quarantined through EMS
- B . Endpoints will be banned on FortiGate
- C . An email notification will be sent for compromised endpoints
- D . Endpoints will be quarantined through FortiSwitch
