Fortinet FCP_FGT_AD-7.4 Übungsprüfungen
Zuletzt aktualisiert am 26.04.2025- Prüfungscode: FCP_FGT_AD-7.4
- Prüfungsname: FCP - FortiGate 7.4 Administrator
- Zertifizierungsanbieter: Fortinet
- Zuletzt aktualisiert am: 26.04.2025
Which two types of traffic are managed only by the management VDOM? (Choose two.)
- A . FortiGuard web filter queries
- B . PKI
- C . Traffic shaping
- D . DNS
Which NAT method translates the source IP address in a packet to another IP address?
- A . DNAT
- B . SNAT
- C . VIP
- D . IPPOOL
Refer to the exhibit.
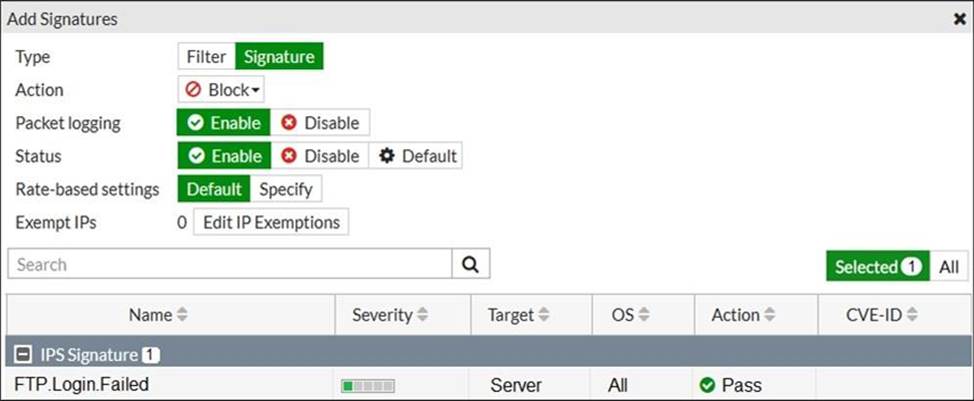
Review the Intrusion Prevention System (IPS) profile signature settings.
Which statement is correct in adding the FTP .Login.Failed signature to the IPS sensor profile?
- A . Traffic matching the signature will be silently dropped and logged.
- B . The signature setting uses a custom rating threshold.
- C . The signature setting includes a group of other signatures.
- D . Traffic matching the signature will be allowed and logged.
Which statement is correct regarding the use of application control for inspecting web applications?
- A . Application control can identify child and parent applications, and perform different actions on them.
- B . Application control signatures are organized in a nonhierarchical structure.
- C . Application control does not require SSL inspection to identify web applications.
- D . Application control does not display a replacement message for a blocked web application.
Which two statements about the application control profile mode are true? (Choose two.)
- A . It uses flow-based scanning techniques, regardless of the inspection mode used.
- B . It cannot be used in conjunction with IPS scanning.
- C . It can be selected in either flow-based or proxy-based firewall policy.
- D . It can scan only unsecure protocols.
What is the effect of enabling auto-negotiate on the phase 2 configuration of an IPsec tunnel?
- A . FortiGate automatically negotiates different local and remote addresses with the remote peer.
- B . FortiGate automatically negotiates a new security association after the existing security association expires.
- C . FortiGate automatically negotiates different encryption and authentication algorithms with the remote peer.
- D . FortiGate automatically brings up the IPsec tunnel and keeps it up, regardless of activity on the IPsec tunnel.
What is eXtended Authentication (XAuth)?
- A . It is an IPsec extension that forces remote VPN users to authenticate using their local ID.
- B . It is an IPsec extension that forces remote VPN users to authenticate using their credentials (username and password).
- C . It is an IPsec extension that authenticates remote VPN peers using a pre-shared key.
- D . It is an IPsec extension that authenticates remote VPN peers using digital certificates.
What are two benefits of flow-based inspection compared to proxy-based inspection? (Choose two.)
- A . FortiGate uses fewer resources.
- B . FortiGate performs a more exhaustive inspection on traffic.
- C . FortiGate adds less latency to traffic.
- D . FortiGate allocates two sessions per connection.
An administrator needs to create a tunnel mode SSL-VPN to access an internal web server from the Internet. The web server is connected to port1. The Internet is connected to port2. Both interfaces belong to the VDOM named Corporation.
What interface must be used as the source for the firewall policy that will allow this traffic?
- A . ssl.root
- B . ssl.Corporation
- C . port2
- D . port1
Which two statements about antivirus scanning in a firewall policy set to proxy-based inspection mode, are true? (Choose two.)
- A . A file does not need to be buffered completely before it is moved to the antivirus engine for scanning.
- B . The client must wait for the antivirus scan to finish scanning before it receives the file.
- C . FortiGate sends a reset packet to the client if antivirus reports the file as infected.
- D . If a virus is detected, a block replacement message is displayed immediately.
