Fortinet FCSS_SOC_AN-7.4 Übungsprüfungen
Zuletzt aktualisiert am 26.04.2025- Prüfungscode: FCSS_SOC_AN-7.4
- Prüfungsname: FCSS - Security Operations 7.4 Analyst
- Zertifizierungsanbieter: Fortinet
- Zuletzt aktualisiert am: 26.04.2025
How do playbook templates benefit SOC operations?
- A . By providing standardized responses to common security scenarios
- B . By reducing the need for IT personnel
- C . By increasing the complexity of incident response
- D . By serving as a decorative element in the SOC
What is the primary role of managing playbook templates in a SOC?
- A . To ensure that entertainment is provided during breaks
- B . To maintain a catalog of ready-to-deploy response strategies
- C . To manage the cafeteria menu in the SOC
- D . To handle the recruitment of new SOC personnel
Which connector on FortiAnalyzer is responsible for looking up indicators to get threat intelligence?
- A . The FortiGuard connector
- B . The FortiOS connector
- C . The FortiClient EMS connector
- D . The local connector
Refer to the exhibits.
![]()
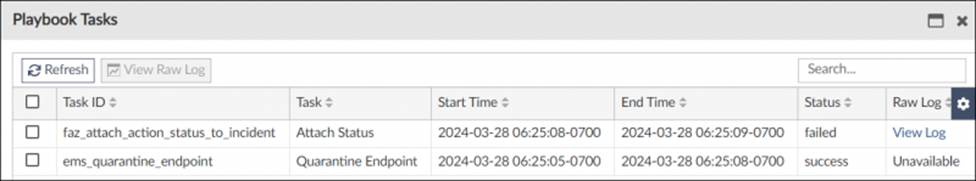
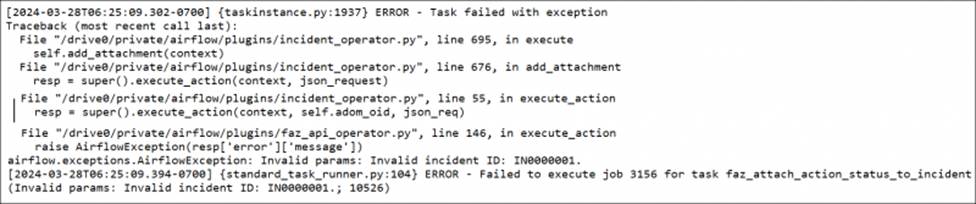
The Quarantine Endpoint by EMS playbook execution failed.
What can you conclude from reviewing the playbook tasks and raw logs?
- A . The playbook executed in an ADOM where the incident does not exist.
- B . The admin user does not have the necessary rights to update incidents.
- C . The local connector is incorrectly configured, which is causing JSON API errors.
- D . The endpoint is quarantined, but the action status is not attached to the incident.
Why is it crucial to configure playbook triggers based on accurate threat intelligence?
- A . To ensure SOC parties are well-attended
- B . To prevent the triggering of irrelevant or false positive actions
- C . To increase the number of digital advertisements
- D . To facilitate easier management of office supplies
Which configuration would enhance the efficiency of a FortiAnalyzer deployment in terms of data throughput?
- A . Lowering the security settings
- B . Reducing the number of backup locations
- C . Increasing the number of collectors
- D . Decreasing the report generation frequency
Which MITRE ATT&CK technique category involves collecting information about the environment and systems?
- A . Credential Access
- B . Discovery
- C . Lateral Movement
- D . Exfiltration
Which elements should be included in an effective SOC report?
(Choose Three)
- A . Detailed analysis of every logged event
- B . Summary of incidents and their statuses
- C . Recommendations for improving security posture
- D . Marketing analysis for the quarter
- E . Action items for follow-up
Which of the following are critical when analyzing and managing events and incidents in a SOC?
(Choose Two)
- A . Rapid identification of false positives
- B . Immediate escalation for all alerts
- C . Immediate escalation for all alerts
- D . Periodic system downtime for maintenance
Review the following incident report.
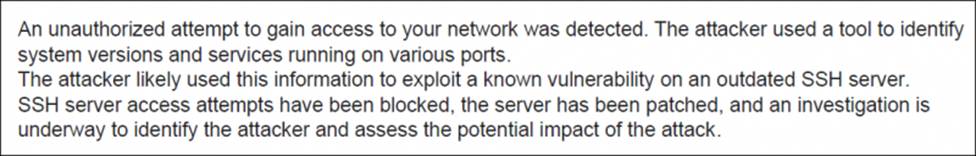
Which two MITRE ATT&CK tactics are captured in this report? (Choose two.)
- A . Defense Evasion
- B . Priviledge Escalation
- C . Reconnaissance
- D . Execution
