Huawei H12-831_V1.0 Übungsprüfungen
Zuletzt aktualisiert am 27.04.2025- Prüfungscode: H12-831_V1.0
- Prüfungsname: HCIP-Datacom-Advanced Routing & Switching Technology V1.0
- Zertifizierungsanbieter: Huawei
- Zuletzt aktualisiert am: 27.04.2025
Which of the following is not included in the OSPF Hello message?
- A . Router ID
- B . Process ID
- C . Area ID
- D . Network Mask
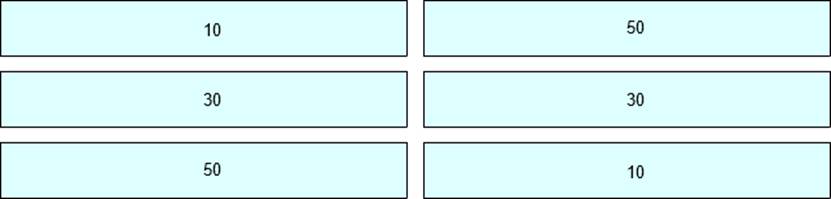
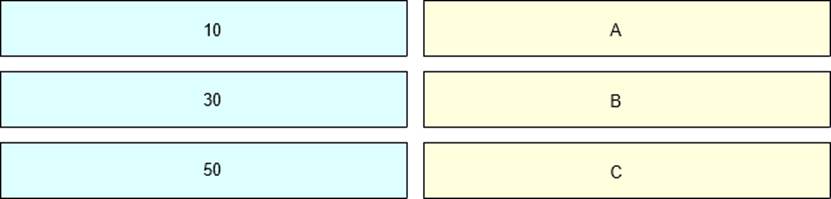
For the OSPF network shown in the figure, please drag the values on the left to the correct position so that the traffic from PC1 to PC2 is PC1-R1-R3-R2-PC2; the traffic from PC2 to PC1 is PC2-R2-R1-PC1.
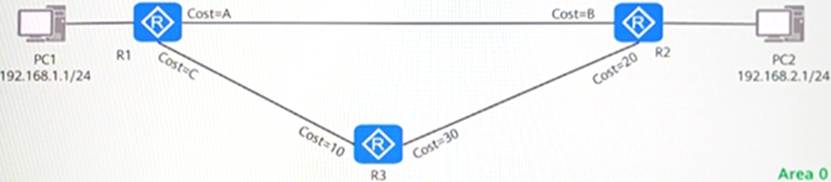
In the OSPF network shown in the figure, the cost value of the link is marked in the figure. R1 has enabled OSPP IP FR and configured the "maximum load-balancing 8" command in the OSPF process. Which of the following is the cost value of reaching 10.0.35.0/24 in R1’s routing table?

- A . 10
- B . 30
- C . 20
- D . 40
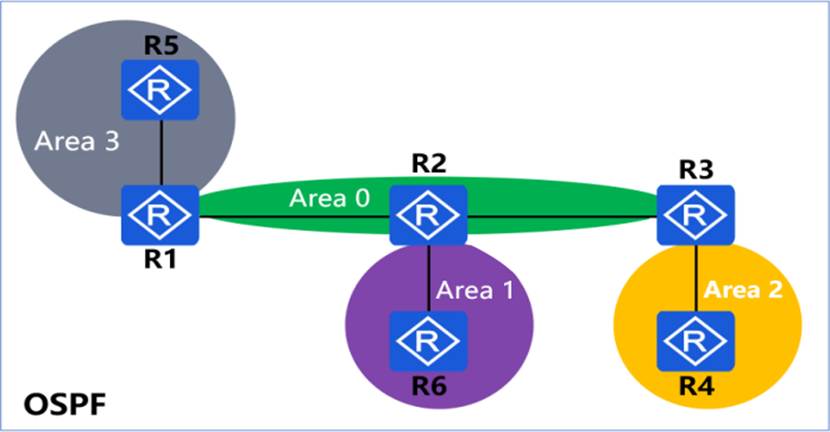
In the OSPF network shown in the figure, the area numbers are marked in the figure. Area 1 is a stub area, area 2 is a totally stub area, and area 3 is an NSSA area. Which of the following types of LSAs will not appear in areas 1, 2, and 3?
- A . Type1
- B . Type3
- C . Type4
- D . Type2
If the cutover preparation is insufficient, which of the following problems may occur? (Multiple choice)
- A . A single board suddenly fails, but there is no spare board
- B . Failure to arrive at the cutover site at the scheduled time
- C . If you do not bring a network cable tester and the port cannot be UP, you cannot determine whether it is a port hardware failure or a cable failure.
- D . Cutover failed, configuration files were not backed up, resulting in service rollback failure
MPLS determines the upstream and downstream relationship based on the data forwarding direction. The MPLS label message is sent from the upstream LSR and received and processed by the downstream LSR. Similarly, the release of MPLS labels is also distributed one by one from upstream to downstream.
- A . True
- B . False
To prevent attackers from forging BGP messages to attack devices, you can protect devices by configuring the CTSM function to detect the range of TTL values in the IP message header. If a device is configured with "peer xxxx valid-ttl-hops 100", the valid range of TTL values of the detected messages is [(), 255].
Which of the following reasons will cause Telnet login failure of network devices? (Multiple choice)
- A . Telnet port is disabled
- B . The Telnet service function of the network device is not enabled
- C . Username and password are wrong
- D . The client’s IP address is blocked
In the IS-IS IPv6 network shown in the figure, the interfaces of R1 and R2 both have two IPv6 addresses. Since the prefix lengths of the IPv6 addresses of R1 and R2 are different, they cannot establish a neighbor relationship.

- A . True
- B . False
When an IP packet enters the MPLS domain, the ingress node checks the Tunnel ID corresponding to the source IP address. When the Tunnel ID is not 0x0, the ingress node performs MPLS forwarding on the packet.
- A . True
- B . False