Microsoft AZ-801 Übungsprüfungen
Zuletzt aktualisiert am 24.04.2025- Prüfungscode: AZ-801
- Prüfungsname: Configuring Windows Server Hybrid Advanced Services
- Zertifizierungsanbieter: Microsoft
- Zuletzt aktualisiert am: 24.04.2025
You are evaluating the technical requirements tor Cluster2.
What is the minimum number of Azure Site Recovery Providers that you should install?
- A . 1
- B . 4
- C . 12
- D . 16
You have an Azure subscription. The subscription contains a virtual machine named VM1 that runs Windows Server.
The subscription contains the storage accounts shown in the following table.
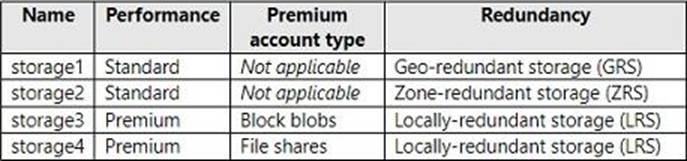
You plan to enable boot diagnostics for VM1.
You need to configure storage for the boot diagnostics logs and snapshots.
Which storage account should you use?
- A . storage1
- B . storage2
- C . storage3
You have 200 Azure virtual machines.
You create a recovery plan in Azure Site Recovery to fail over all the virtual machines to an Azure region. The plan has three manual actions.
You need to replace one of the manual actions with an automated process.
What should you use?
- A . an Azure Desired State Configuration (DSC) virtual machine extension
- B . an Azure Automation runbook
- C . an Azure PowerShell function
- D . a Custom Script Extension on the virtual machines
Your company uses Storage Spaces Direct.
You need to view the available storage in a Storage Space Direct storage pool.
What should you use?
- A . System Configuration
- B . File Server Resource Manager (FSRM)
- C . the Get-ScorageFileServer cmdlet
- D . Failover Cluster Manager
You have five Azure virtual machines. You have a dedicated Azure Storage account to collect performance data. You need to send the collected data directly to the Azure Storage account.
What should you install on the virtual machines?
- A . the Telegraf agent
- B . the Azure Monitor agent
- C . the Dependency agent
- D . the Azure Diagnostics extension
- E . the Azure Connected Machine agent
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a failover cluster named Cluster! that hosts an application named Appl.
The General tab in App1 Properties is shown in the General exhibit (Click the General tab.)
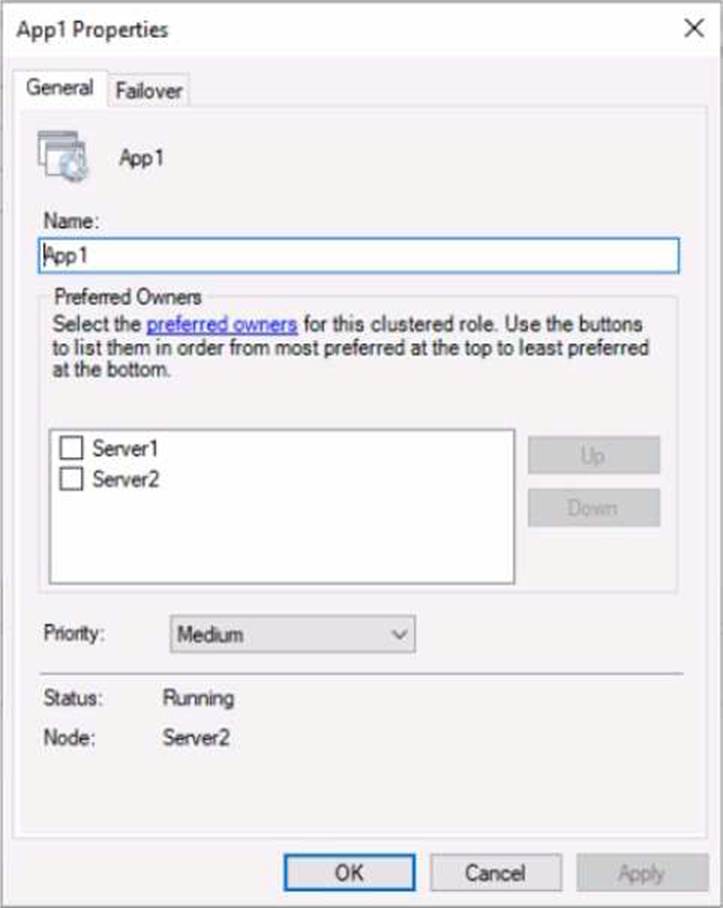
The Failover tab in App1 Properties is shown in the Failover exhibit. (Click the Failover tab.)
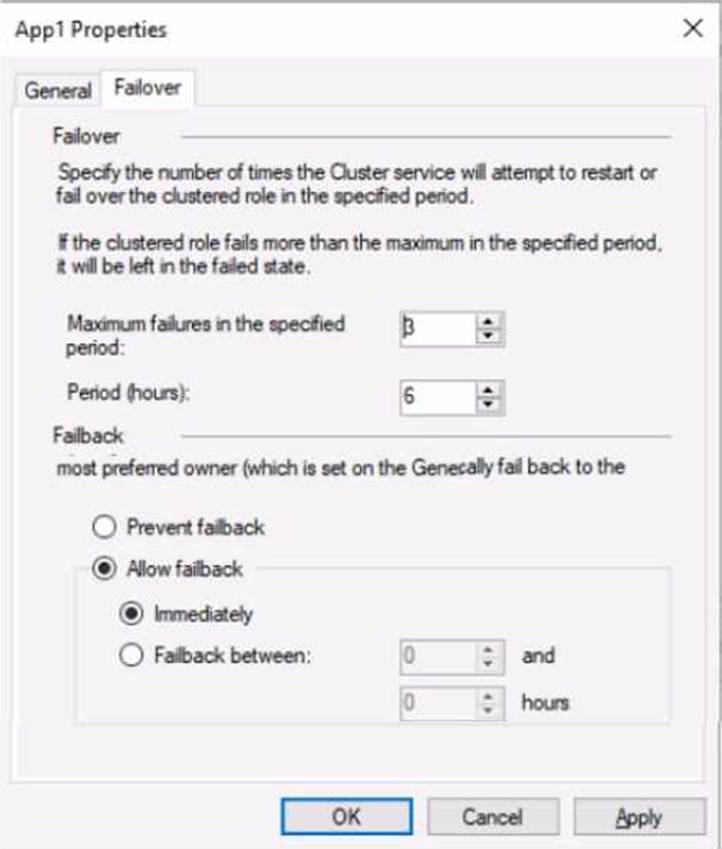
Server2 shuts down unexpectedly.
You need to ensure that when you start Server2, App1 continues to run on Server2.
Solution: You pause the Server1 node in Cluster1 and then start Server1.
Does this meet the goal?
- A . Yes
- B . No
Your network contains an Active Directory Domain Services (AD DS) domain All domain members have Microsoft Defender Credential Guard with UEFI tock configured in the domain you deploy a server named Server1 that runs Windows Server. You disable Credential Guard on Server1. You need to ensure that Server1 is MOST subject to Credential Guard restrictions.
What should you do next?
- A . Run the Device Guard and Credential Guard hardware readiness tool
- B . Disable the Turn on Virtual nation Based Security group policy setting
- C . Run dism and specify the /Disable-Feature and /FeatureName:IsolatedUserMode parameters
You have an Azure virtual machine named VM1 that runs Windows Server.
When you attempt to install the Azure Performance Diagnostics extension on VM I, the installation fails.
You need to identify the cause of the installation failure.
What are two possible ways to achieve the goal? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
- A . Sign in to VM1 and verify the WaAppAgentlog file.
- B . From the Azure portal, view the alerts for VM1.
- C . From the Azure portal, view the activity log for VM1.
- D . Sign into VM1 and verify the MonitoringAgentlog file.
Topic 3, Misc. Questions
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a server named Server1 that runs Windows Server.
You need to ensure that only specific applications can modify the data in protected folders on Server1.
Solution: From Virus & threat protection, you configure Controlled folder access.
Does this meet the goal?
- A . Yes
- B . No
HOTSPOT
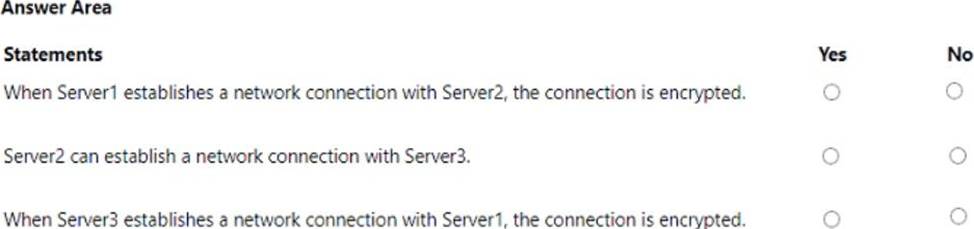
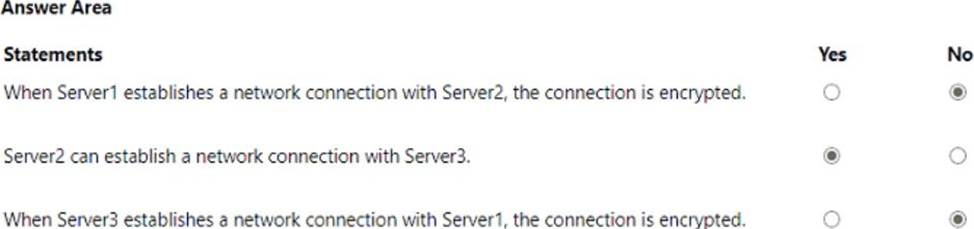
Your network contains an Active Directory Domain Services (AD DS) domain. The domain contains three servers named Server1, Server2, and Server3 that run Windows Server. All the servers are on the same network and have network connectivity.
On Server1, Windows Defender Firewall has a connection security rule that has the following settings:
• Rule Type: Server-to-server
• Endpoint 1: Any IP address
• Endpoint 2: Any IP address
• Requirements: Require authentication for inbound connections and request authentication for outbound connections
• Authentication Method: Computer (Kerberos V5)
• Profile: Domain, Private, Public
• Name: Rule1
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.